End-to-End Encryption: A Complete Guide for Private Communication
What is End-to-End Encryption?
End-to-end encryption (E2EE) is a secure communication method that prevents third parties—including service providers, hackers, and even government agencies—from accessing data while it's transferred from one system or device to another. In an E2EE system, only the communicating users can read the messages. No intermediary, not even the platform hosting the communication, can access the cryptographic keys needed to decrypt the conversation.
The "end-to-end" in E2EE refers to the fact that the encryption covers the entire journey of a message, from its origin (one end) to its destination (the other end). This distinguishes it from other forms of encryption, which might only protect data during transit but allow service providers to access unencrypted data at either endpoint.
How End-to-End Encryption Works
Understanding the technical aspects of E2EE can help you appreciate its security benefits:
Key Generation and Exchange
When you initialize a secure conversation with someone using E2EE:
- Your device generates a public key and a private key.
- The public key can be shared with anyone, while the private key remains securely on your device.
- Your contact's device does the same, generating their own key pair.
- You and your contact exchange public keys, either directly or through a trusted server.
Message Encryption Process
When you send a message to your contact:
- Your device encrypts the message using your contact's public key.
- The encrypted message travels through the network to your contact.
- Even if intercepted during transit, the encrypted message appears as gibberish without the corresponding private key.
- Upon receipt, your contact's device uses their private key to decrypt the message.
Why End-to-End Encryption Matters
In today's digital landscape, E2EE has become increasingly important for several compelling reasons:
Privacy Protection
E2EE ensures that sensitive information remains confidential between you and your intended recipient. This is crucial for:
- Personal communications about health, finances, or other private matters
- Business discussions containing proprietary information
- Sharing confidential documents or credentials
- Protecting conversations from data mining for advertising purposes
Security Against Data Breaches
Even if a service provider experiences a data breach, your encrypted messages remain secure because:
- The service never has access to the decryption keys
- The encrypted data is meaningless without the private keys
- Hackers would need to compromise individual devices to access the content
Protection from Surveillance
E2EE provides critical protection against various forms of surveillance:
- Prevents service providers from being compelled to provide readable message content
- Reduces vulnerability to mass surveillance programs
- Protects journalists, activists, and others who may be targeted for their communications
Security Tip
While E2EE protects the content of your messages, it doesn't hide metadata—information about who is communicating with whom, when, and how often. For maximum privacy, consider combining E2EE with other privacy tools like VPNs or self-destructing messages.
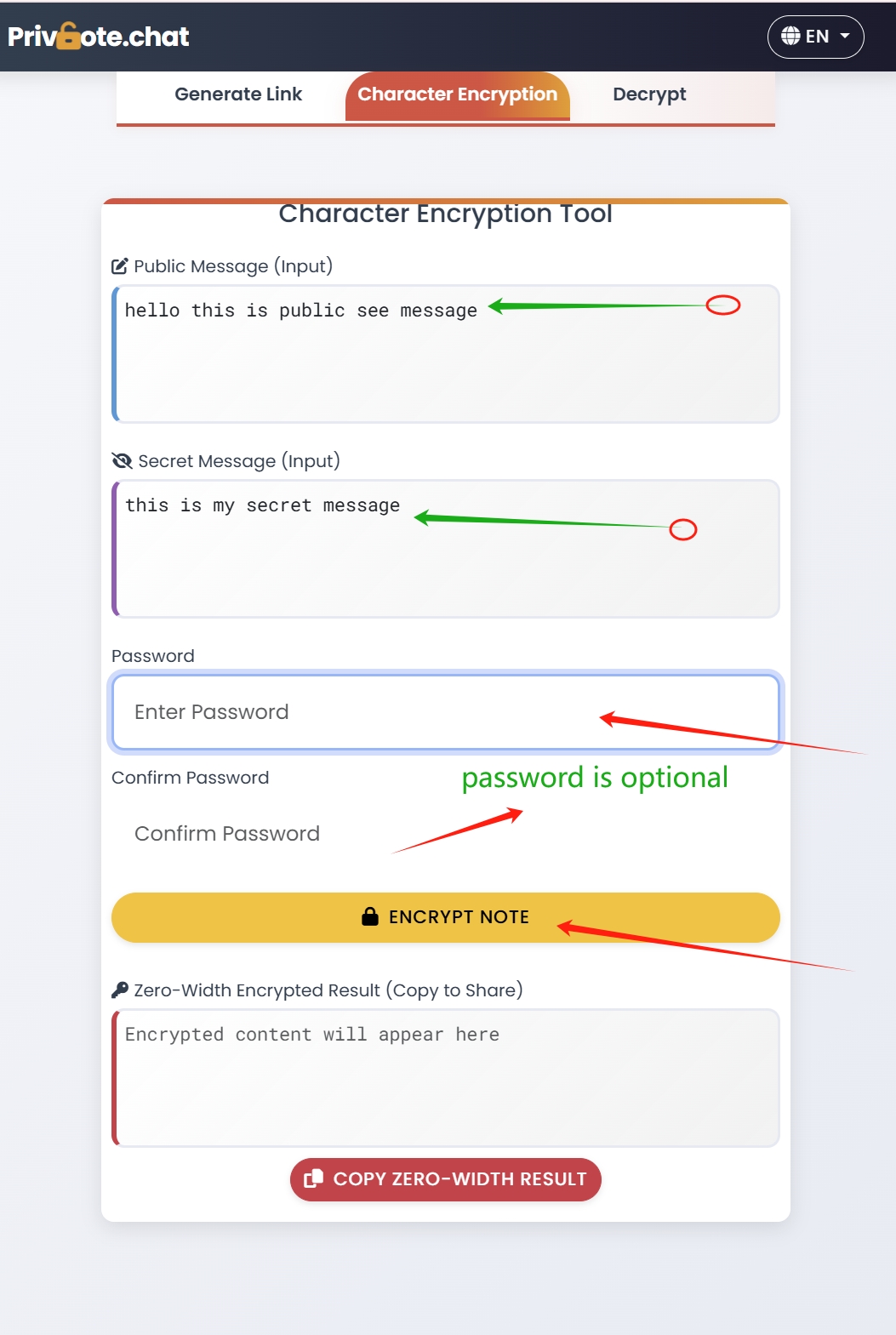
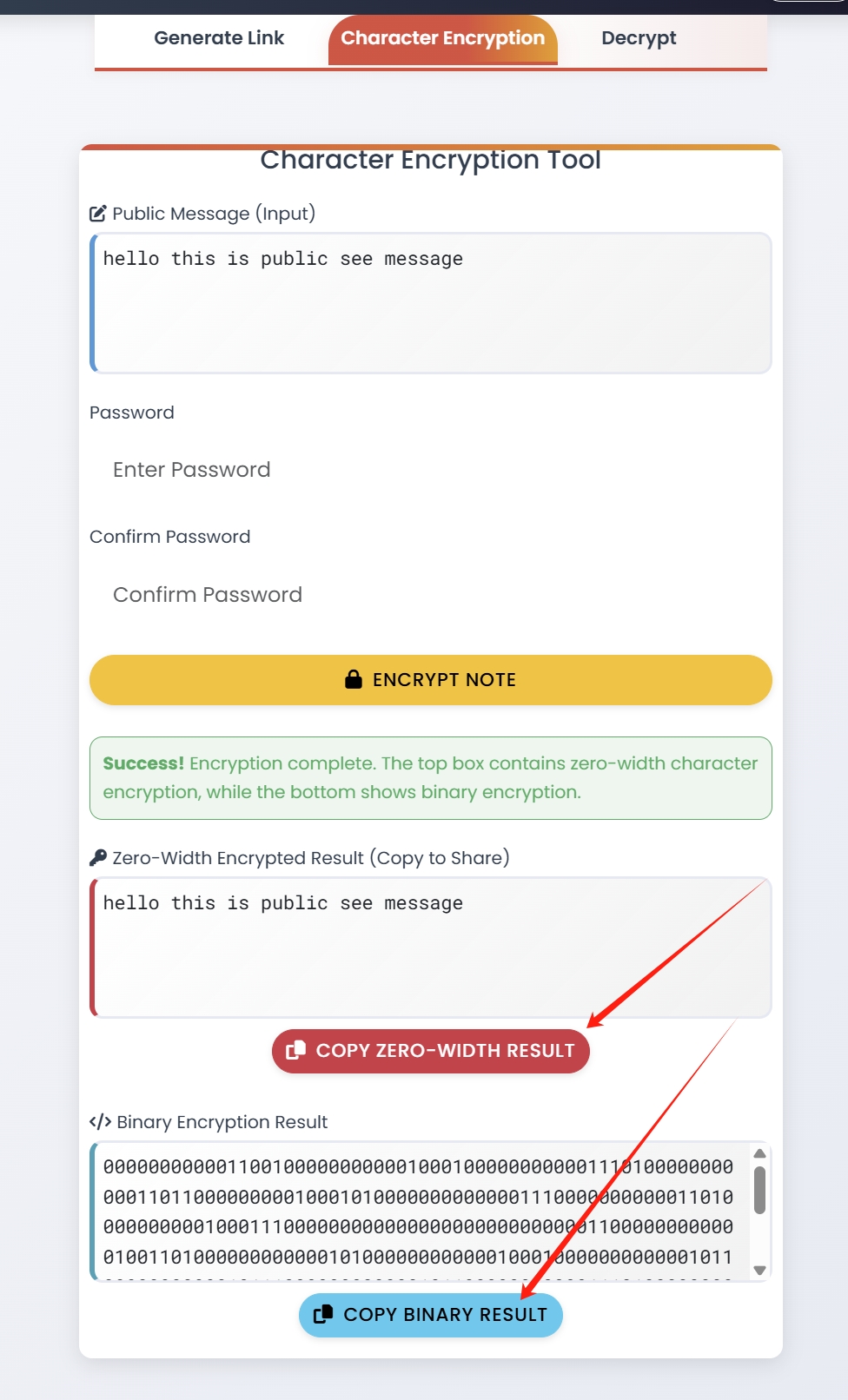
E2EE vs. Self-Destructing Messages: Complementary Security
End-to-end encryption and self-destructing messages address different aspects of communication security. Let's examine how Privnote combines both approaches:
As illustrated above, Privnote encrypts messages on the client side before sending them to the server, ensuring true end-to-end encryption. Combined with automatic destruction after reading, this provides comprehensive protection:
End-to-End Encryption
Protects: Data in transit
Prevents: Interception by third parties
Weakness: Messages remain on devices indefinitely
Self-Destructing Messages
Protects: Data persistence
Prevents: Future access to message content
Weakness: Doesn't protect against interception
Using both technologies together provides comprehensive protection: E2EE secures the transmission of your message, while self-destructing functionality ensures the message doesn't remain accessible indefinitely after it's been read.
The History and Evolution of End-to-End Encryption
End-to-end encryption has a rich history that has evolved alongside computing technology:
Early Days of Encryption
The conceptual foundations of modern encryption date back centuries:
- 1970s: The development of the RSA algorithm by Rivest, Shamir, and Adleman created the first practical public-key cryptosystem
- 1991: Phil Zimmermann released PGP (Pretty Good Privacy), one of the first widely available E2EE tools for email
- 1990s: The crypto wars began as governments sought to restrict strong encryption technologies
Modern E2EE Development
The growth of the internet and mobile communications brought new developments:
- 2004: Off-the-Record (OTR) Messaging protocol introduced perfect forward secrecy to instant messaging
- 2011-2013: The Snowden revelations highlighted mass surveillance, driving demand for E2EE
- 2014-2016: Signal Protocol developed, establishing a new standard for secure messaging
- 2016-Present: Widespread adoption of E2EE in mainstream applications like WhatsApp and Facebook Messenger

The Technical Foundations: Cryptographic Principles Behind E2EE
To truly understand end-to-end encryption, it's helpful to explore the core cryptographic principles that make it possible:
Asymmetric Cryptography (Public-Key Encryption)
The foundation of modern E2EE is asymmetric cryptography:
- Uses mathematically related key pairs: one public (for encryption) and one private (for decryption)
- Based on mathematical problems that are computationally difficult to solve, such as integer factorization
- Allows secure communication without requiring a pre-shared secret key
Perfect Forward Secrecy (PFS)
Modern E2EE protocols implement PFS to enhance security:
- Generates ephemeral session keys for each conversation
- Ensures that if a private key is compromised in the future, past conversations remain secure
- Requires compromising individual session keys to decrypt past messages
Digital Signatures
Authentication is ensured through digital signatures:
- Proves the identity of the sender
- Verifies that messages haven't been tampered with in transit
- Created by encrypting a message digest with the sender's private key
Technical Example
In modern E2EE implementations like the Signal Protocol, multiple layers of keys work together:
- Identity Keys: Long-term keys that identify users
- Signed Pre-Keys: Medium-term keys signed by the Identity Key
- One-Time Pre-Keys: Used once per session initialization
- Session Keys: Derived through a Diffie-Hellman key exchange and ratcheted forward for each message
E2EE for Different User Types: Personal, Business, and High-Security Needs
Different users have different requirements for end-to-end encryption. Understanding your needs can help you choose the right solutions:
Personal Users
Individual users typically prioritize:
- Ease of use: Simple setup and operation without technical knowledge
- Cross-platform availability: Access across multiple devices and operating systems
- Social adoption: Encryption that works with existing contacts
- Recommended solutions: Signal, WhatsApp, Privnote for sensitive information sharing
Business Users
Organizations require additional features:
- Administrative controls: User management and policy enforcement
- Compliance capabilities: Data retention and legal requirements
- Integration: Works with existing business systems and workflows
- Recommended solutions: Wickr Enterprise, Cisco Secure Communications, ProtonMail for Business
High-Security Users
Journalists, activists, security professionals, and others with elevated threat models need:
- Maximum security: Strongest available encryption with minimal metadata
- Independent verification: Open-source code for security audits
- Anonymity features: Options to minimize identifiable information
- Recommended solutions: Signal with additional security settings, PGP for email, self-hosted instances when possible
Common Misconceptions About End-to-End Encryption
There are several widespread misunderstandings about E2EE that can lead to a false sense of security or unnecessary concern:
Myth
"E2EE makes communication completely anonymous."
Fact
E2EE protects content but not metadata like who's talking to whom, when, and how often.
Myth
"E2EE is only used by people with something to hide."
Fact
E2EE is a standard security measure used by millions of ordinary people and businesses to protect sensitive information.
Myth
"If an app claims to use encryption, it must be secure."
Fact
Many apps use weak encryption, have implementation flaws, or only encrypt data in transit, not end-to-end.
End-to-End Encryption Platforms and Solutions
There are numerous applications and services that implement E2EE, each with different features and use cases:
Messaging Apps with E2EE
- Signal: Open-source messaging app with robust E2EE for texts, calls, and file sharing
- WhatsApp: Popular messaging platform that implements the Signal protocol for E2EE
- Telegram: Offers "Secret Chats" with E2EE (note that regular chats are not E2EE by default)
- iMessage: Apple's messaging service with E2EE between Apple devices
Email with E2EE
- ProtonMail: Email service with built-in E2EE
- PGP/GPG: Standards that can add E2EE to existing email platforms
- Tutanota: Secure email service with integrated encryption
Secure Note Services
- Privnote: Combines E2EE with self-destructing functionality for maximum security
- Standard Notes: E2EE note-taking application
- Joplin: Open-source note application with optional E2EE
File Sharing with E2EE
- Tresorit: Cloud storage with client-side encryption
- Sync.com: Zero-knowledge cloud storage
- Keybase: E2EE file sharing platform
Future Trends in Encryption Technology
As technology evolves, so too will encryption methods. Here are some emerging trends that will shape the future of secure communications:
Quantum-Resistant Encryption
Quantum computing presents both challenges and opportunities for encryption:
- Quantum computers may eventually break current public-key encryption algorithms
- Post-quantum cryptography is being developed to resist quantum attacks
- NIST is currently standardizing quantum-resistant algorithms
- Forward-thinking E2EE applications are preparing to implement these new algorithms
Homomorphic Encryption
This revolutionary technology could change how we think about encrypted data:
- Allows computations to be performed on encrypted data without decrypting it
- Could enable secure cloud-based processing while maintaining privacy
- May eventually be incorporated into E2EE messaging platforms for enhanced features
Decentralized Identity and Encryption
Blockchain and decentralized technologies are influencing encryption:
- Self-sovereign identity systems for more secure key management
- Decentralized key verification to reduce reliance on centralized authorities
- Smart contract-based secure messaging protocols that eliminate central servers entirely
Usability Improvements
The future of E2EE will focus on making strong security more accessible:
- Simplified key management that maintains security while reducing user burden
- Cross-platform standards for E2EE messaging interoperability
- Better UX design to make security features more intuitive
- Automated security checks and recommendations built into applications
Future-Proofing Your Security
To stay ahead of encryption developments, regularly update your security software, follow trusted security experts, and be prepared to adopt new technologies as they become available.
Frequently Asked Questions About End-to-End Encryption
While E2EE messages can be intercepted during transmission, they cannot be decrypted without the private key, which is stored only on the recipient's device. This makes properly implemented E2EE extremely resistant to interception attacks. However, if an endpoint (device) is compromised, the messages can be accessed after decryption.
Properly implemented E2EE mathematically prevents anyone, including service providers and governments, from accessing the content of encrypted messages. However, some approaches to circumvent E2EE include:
- Legal demands for companies to modify their software to include backdoors (which would compromise E2EE for all users)
- Targeting the endpoints rather than the encryption (e.g., using malware to access messages before encryption or after decryption)
- Exploiting implementation vulnerabilities in specific E2EE applications
This is why it's important to use well-audited, open-source E2EE solutions whenever possible.
Modern E2EE implementations have minimal performance impact that is typically imperceptible to users. The encryption and decryption processes are highly optimized and executed quickly on modern devices. Some performance considerations include:
- Initial key exchange might add a small delay when starting a new conversation
- Very large file transfers might experience slightly more processing time
- Older or resource-constrained devices might experience more noticeable delays
For most users on modern devices, the security benefits far outweigh any minor performance impacts.
Yes, E2EE is just one component of a comprehensive security approach. Other important security measures include:
- Strong, unique passwords for all accounts and devices
- Two-factor authentication where available
- Regular software updates to patch security vulnerabilities
- Device encryption to protect stored data
- VPNs or other tools to protect metadata and browsing activity
- Security-focused practices like screen locks and careful handling of sensitive information
E2EE protects your communications in transit, but a multi-layered security approach provides more comprehensive protection.
Verifying E2EE is in place and working correctly involves several steps:
- Use applications with transparent, open-source code that has been audited by security professionals
- Look for security indicators within the app (e.g., lock icons, "encrypted" labels)
- Use the application's key verification features to confirm you're connected to the right person
- For many secure messaging apps, you can scan QR codes or compare "safety numbers" with your contact through an out-of-band channel
- Watch for security notifications about changes to encryption keys
If an application doesn't provide a way to verify encryption is in place, that might be a red flag about its security claims.
Real-World Applications: E2EE Success Stories
End-to-end encryption has proven its value in numerous real-world scenarios:
Journalism and Source Protection
E2EE has become an essential tool for journalists:
- Enables confidential communication with sensitive sources
- Protects whistleblowers from identification
- Secures unpublished stories and research from interception
- Organizations like the Freedom of the Press Foundation actively promote E2EE tools for journalists
Healthcare Communications
The healthcare industry has embraced E2EE to protect patient information:
- Secure doctor-patient communications that maintain privacy
- Protection of sensitive test results and diagnoses
- Compliant sharing of protected health information
- Telemedicine platforms with built-in E2EE for virtual visits
Business Negotiations and Intellectual Property
Companies rely on E2EE to protect valuable business information:
- Secure discussions about mergers and acquisitions
- Protection of trade secrets and proprietary information
- Confidential communication with clients and partners
- Secure internal discussions about unreleased products or services
Limitations and Challenges of E2EE
While E2EE provides strong security, it's important to understand its limitations:
Endpoint Security
E2EE protects data in transit, but it cannot protect against compromised endpoints (devices):
- If malware is present on your device, it could capture messages before encryption or after decryption
- Physical access to an unlocked device can expose messages
- Screen capture or "over-the-shoulder" viewing bypasses E2EE protection
Implementation Vulnerabilities
The security of E2EE depends on proper implementation:
- Flawed cryptographic implementations can create vulnerabilities
- Backdoors or "key escrow" systems compromise the integrity of E2EE
- Closed-source applications cannot be independently verified for security
Regulatory Challenges
E2EE faces increasing regulatory scrutiny:
- Some jurisdictions have attempted to require "backdoors" for law enforcement
- Balancing security, privacy, and legitimate law enforcement needs remains controversial
- Regulations may limit the deployment or strength of E2EE in some contexts
Best Practices for Using End-to-End Encryption
To maximize the security benefits of E2EE, follow these best practices:
Verify Security Claims
- Use applications with open-source code that can be audited
- Look for services that have undergone independent security audits
- Be skeptical of vague claims about "military-grade encryption" without specifics
Verify Contacts and Keys
- Use security verification features like QR codes or safety numbers to confirm you're communicating with the intended recipient
- Be alert to warnings about key changes, which could indicate a man-in-the-middle attack
- Verify key fingerprints through a separate communication channel when possible
Secure Your Devices
- Keep operating systems and applications updated with security patches
- Use strong device encryption and authentication
- Install security software to detect malware
- Be cautious about physical access to your devices
Use Ephemeral Messaging
- Enable disappearing messages when available in E2EE applications
- Use services like Privnote for particularly sensitive information that should not persist
- Regularly delete message history even when using E2EE
Conclusion: The Future of Secure Communication
End-to-end encryption has evolved from a niche technology to an essential component of modern digital security. As we've explored throughout this guide, E2EE provides critical protection for personal communications, business data, and sensitive information of all kinds.
In an era of increasing digital surveillance, data breaches, and sophisticated cyber threats, the role of E2EE will only grow more important. The technology continues to evolve, with new approaches being developed to address quantum computing threats and improve usability without sacrificing security.
For individuals concerned about privacy, the combination of E2EE with self-destructing messages provides a comprehensive security approach—protecting both the transmission of information and limiting its persistence after it has been read.
As users become more privacy-conscious, demand for secure communication tools will continue to rise. The companies and platforms that make security and privacy a priority will be best positioned to meet the needs of tomorrow's digital citizens.
By understanding how E2EE works, recognizing its strengths and limitations, and following best practices for secure communication, you can take control of your digital privacy in an increasingly connected world.
Your Next Steps
Ready to enhance your communication security? Here are three actions you can take today:
- Evaluate your current messaging apps and consider switching to those with strong E2EE
- Start using Privnote for sharing sensitive information that shouldn't persist
- Share this guide with friends and family to help them understand the importance of encryption
Remember that digital security is a journey, not a destination. Stay informed about new developments in encryption technology and continue to adapt your practices as the digital landscape evolves.
Ready to experience the benefits of secure, self-destructing messaging? Try Privnote today and add an additional layer of protection to your sensitive communications.