Secure Messaging for Business: Protecting Corporate Communications
The Business Case for Secure Messaging
In today's digital business landscape, the need for secure corporate communications has never been more critical. With data breaches costing companies an average of $4.35 million in 2024 according to IBM's Cost of a Data Breach Report, organizations can no longer afford to treat messaging security as an afterthought.
Business communications often contain sensitive information that, if compromised, could lead to:
- Intellectual property theft
- Competitive disadvantages
- Regulatory compliance violations
- Reputational damage
- Financial losses
While many organizations focus their security efforts on formal documents and databases, day-to-day communications often fly under the radar—creating a significant vulnerability in an otherwise robust security posture.
Regulatory Requirements for Business Communications
Beyond the practical security concerns, businesses across industries face increasingly stringent regulatory requirements regarding data protection and privacy:
GDPR Compliance
The General Data Protection Regulation (GDPR) requires businesses to implement appropriate technical and organizational measures to protect personal data. This includes communications that might contain customer information, employee details, or other personally identifiable information.
Key GDPR principles that apply to business messaging include:
- Data Minimization - Only collect and share what's necessary
- Storage Limitation - Don't retain data longer than needed
- Purpose Limitation - Only use data for its intended purpose
Industry-Specific Regulations
Depending on your industry, additional regulations may apply:
- Healthcare (HIPAA) - Requires strict protection of patient information
- Finance (PCI DSS, GLBA) - Mandates protection of financial data and transactions
- Legal Industry - Subject to attorney-client privilege requirements
- Government Contracting - May require specific security protocols
Implementing Secure Messaging with Self-Destructing Notes
Self-destructing notes offer a powerful solution for businesses looking to enhance their communication security. Here's how to implement them effectively in your organization:
1. Establish a Secure Messaging Policy
Before implementing any technical solution, create a clear policy that outlines:
- What types of information should be shared via secure, ephemeral channels
- When standard email or messaging is appropriate vs. when secure messaging is required
- Who is authorized to share what types of information
- How to properly verify recipient identity before sharing sensitive information
- Recordkeeping requirements for regulatory compliance
2. Train Employees on Secure Messaging Practices
Technology alone isn't enough—employees need to understand:
- How to identify sensitive information that requires secure messaging
- Proper procedures for verifying recipient identity
- How to use self-destructing note platforms correctly
- The risks of circumventing secure messaging policies
Pro Tip
Create a quick reference guide for employees that outlines what types of information should always be shared via secure channels. Include specific examples relevant to your industry and organization.
3. Choose the Right Self-Destructing Note Solution
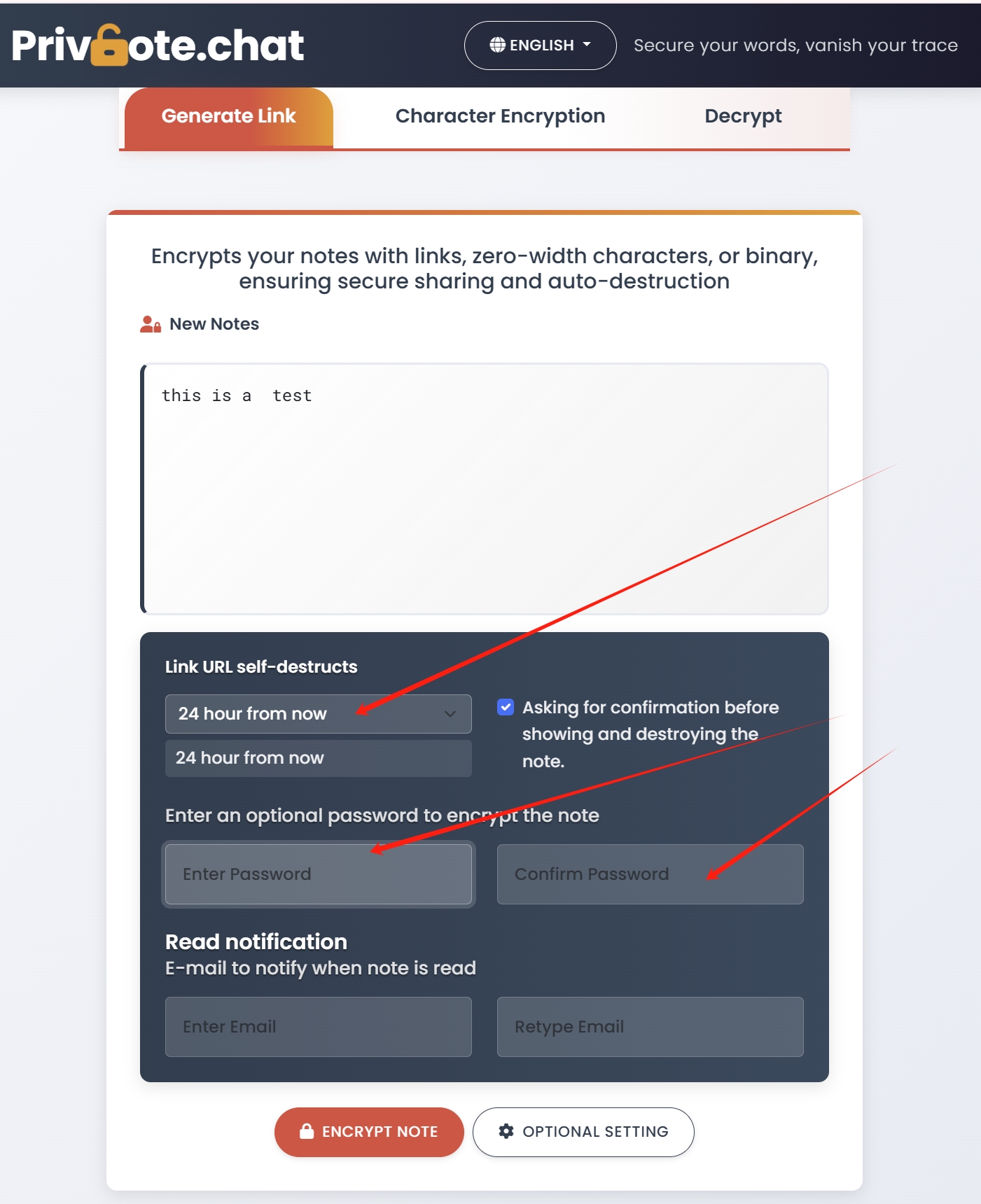
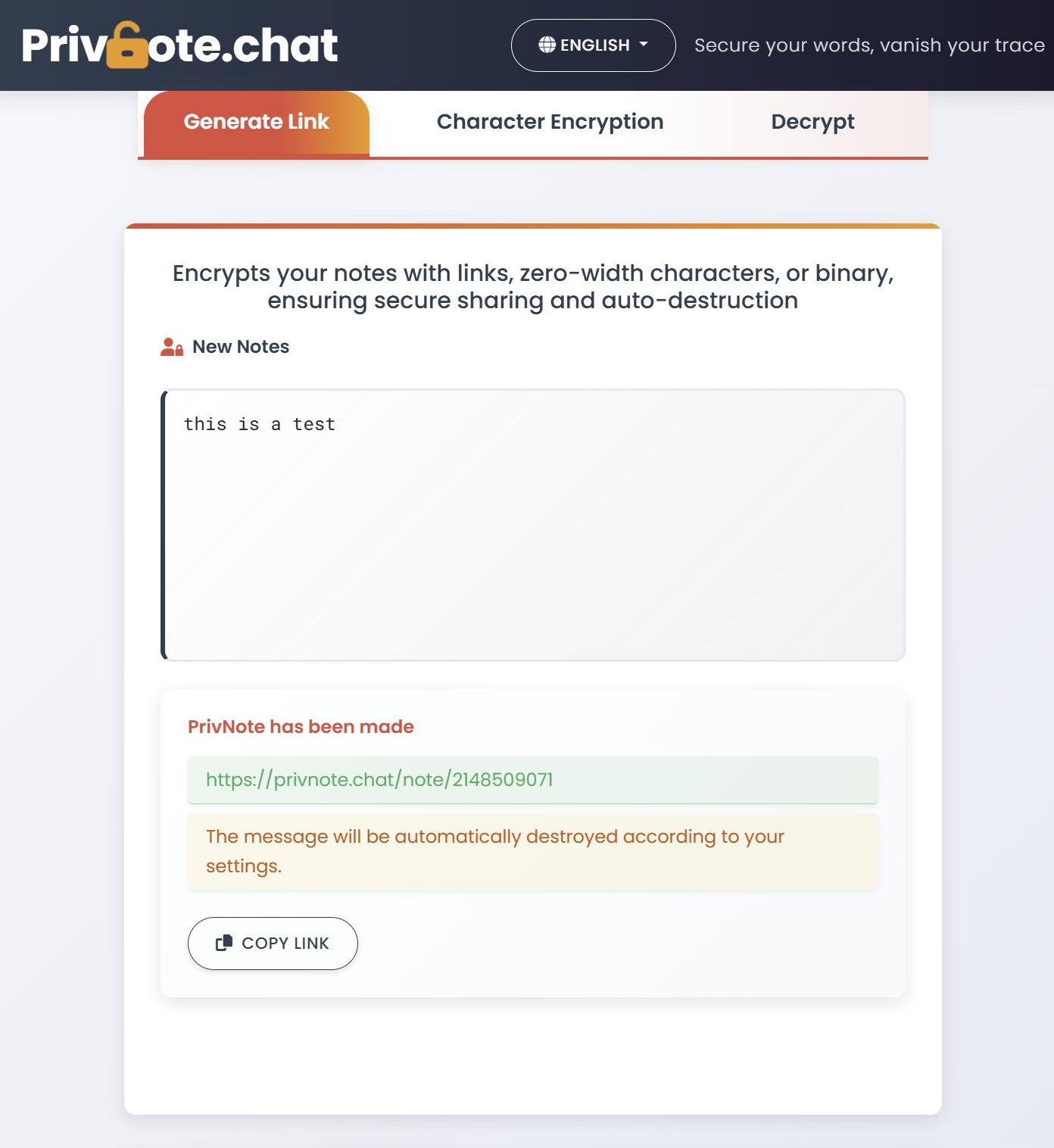
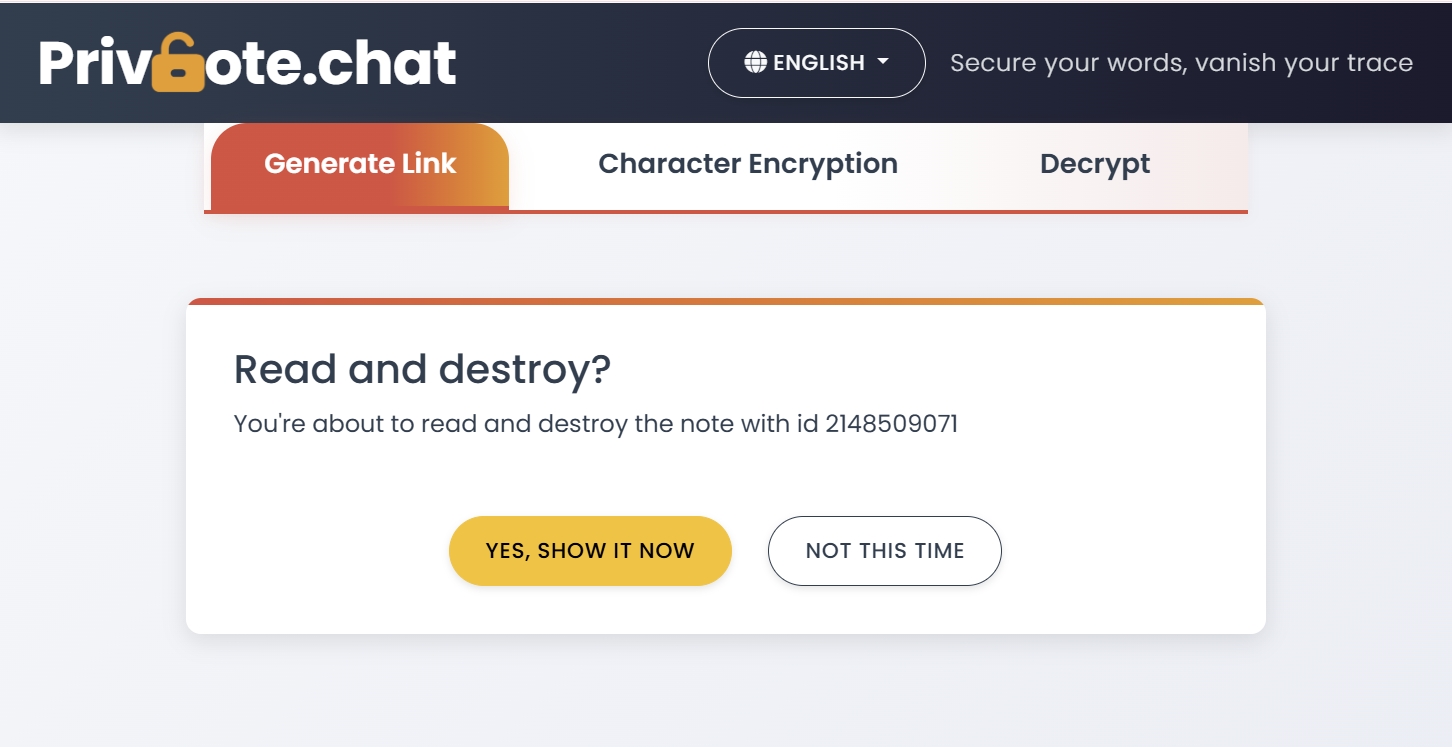
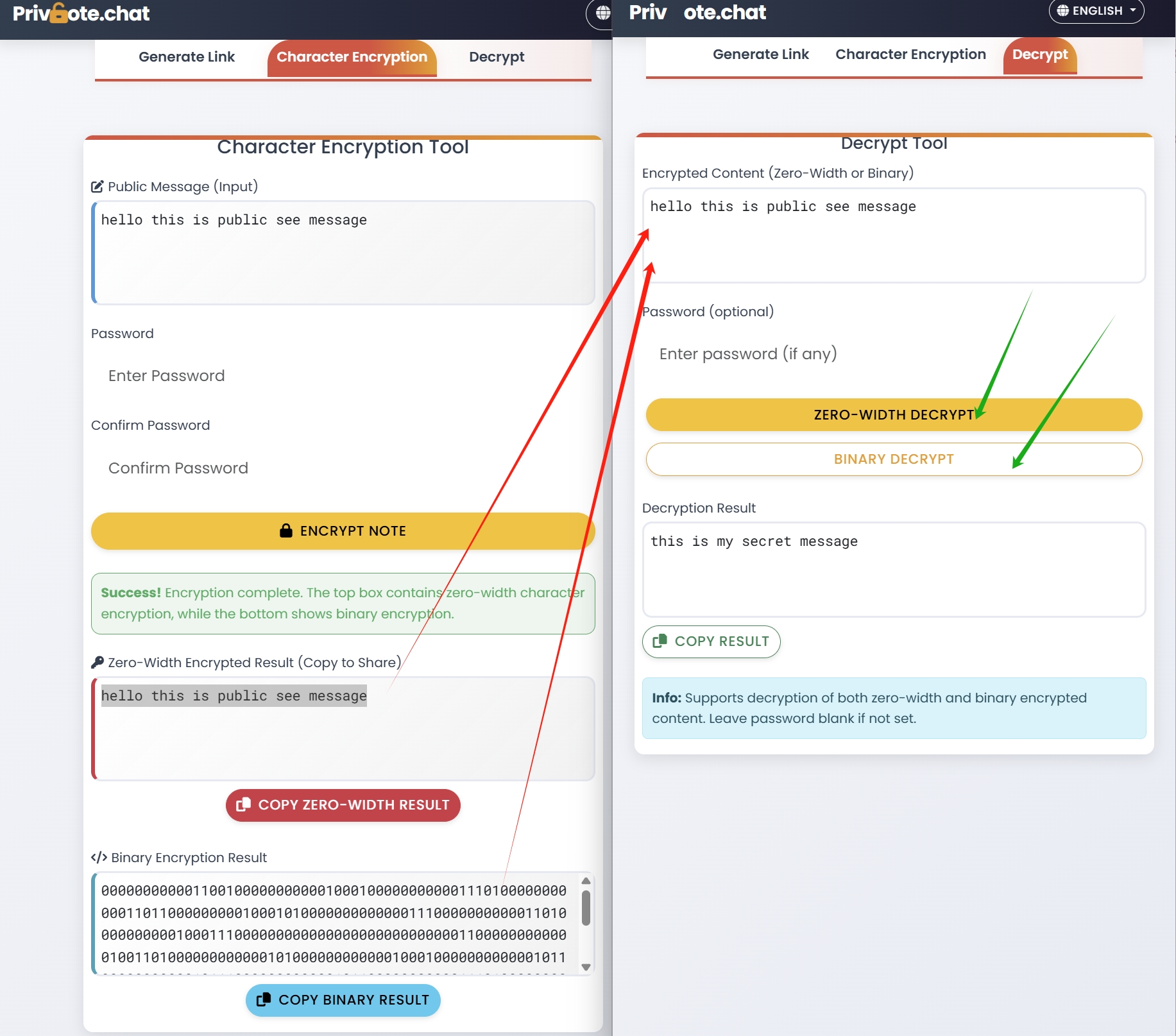
When evaluating platforms like Privnote for business use, consider these key features:
- Password Protection - Additional verification layer for sensitive communications
- Read Receipts - Confirmation when messages have been accessed and destroyed
- Custom Expiration - Set messages to expire after a certain time even if unread
- Zero-Width Encryption - Additional layer of encryption for highest-sensitivity communications
- Audit Capabilities - Logging that messages were sent and received for compliance
Use Cases: When Businesses Should Use Self-Destructing Notes
Executive Communications
Leadership teams often discuss sensitive matters that shouldn't persist in email or chat histories:
- Potential mergers and acquisitions
- Upcoming organizational changes
- Unreleased financial information
- Strategic initiatives and competitive analysis
Human Resources
HR departments handle some of the most sensitive personal information in an organization:
- Sharing salary information with managers
- Discussing employee performance issues
- Communicating about workplace investigations
- Sharing employment verification credentials
IT and Security Teams
Those responsible for securing the organization often need to share sensitive access information:
- Temporary admin credentials
- Server access information
- Recovery codes and emergency access details
- Security vulnerability information prior to patching
Client Communications
Many businesses need to share sensitive information with clients:
- Account credentials or access codes
- Confidential project details
- Contract information prior to finalization
- Financial data and transaction details
Important Consideration
While self-destructing notes are excellent for transitory communications, they are not appropriate for information that must be retained for legal or regulatory reasons. Consult with your legal and compliance teams to determine appropriate retention requirements for different types of business communications.
Integrating Secure Messaging into Business Workflows
For maximum effectiveness, secure messaging solutions should be integrated into your existing business workflows rather than treated as separate tools.
Authentication Integration
Consider how secure messaging tools like Privnote can work with your existing authentication systems:
- Using corporate email addresses to verify recipient identity
- Implementing multi-factor authentication for highly sensitive communications
- Establishing trusted contact lists for quick, secure messaging
Process Documentation
Update your business processes to include guidance on when to use secure messaging:
- Incorporate secure messaging steps into relevant workflow documents
- Add secure messaging checkpoints to compliance checklists
- Document when secure message confirmations should be archived for audit purposes
Conclusion: A Balanced Approach to Business Communications
In the business world, communication needs to balance security, efficiency, and compliance. Self-destructing notes offer a powerful tool that addresses all three concerns when implemented correctly.
By establishing clear policies, providing proper training, and choosing a secure platform like Privnote with business-appropriate features, organizations can significantly reduce the risk of sensitive information leaks while maintaining productivity.
Remember that secure messaging is just one component of a comprehensive data protection strategy. It works best when combined with other security measures like access controls, data classification, and regular security awareness training.
Ready to enhance your organization's communication security? Try Privnote's self-destructing notes for your next sensitive business communication.