Zero-Width Character Encryption: The Invisible Layer of Privacy
Understanding Zero-Width Character Encryption
In the world of digital security, encryption methods typically transform your message into a scrambled, unreadable format that requires a key to decrypt. While effective, these methods make it obvious that something is being hidden. But what if your sensitive message could hide in plain sight, completely invisible to casual observers?
This is precisely what zero-width character encryption accomplishes - a sophisticated form of steganography that conceals your message using invisible characters interspersed within normal, visible text.
Key Concept:
Zero-width character encryption is a form of digital steganography - the practice of concealing information within other non-secret text or data. Unlike traditional encryption that scrambles content, steganography hides the very existence of the secret message.
How Zero-Width Characters Work
Zero-width characters are special Unicode characters that take up no visible space when rendered in text. They were originally designed for specific formatting and linguistic purposes, but they've found a new application in the realm of hidden communication.
Common Zero-Width Characters
| Character | Unicode | Description | Original Purpose |
|---|---|---|---|
ZWSP |
U+200B | Zero-Width Space | Indicates word boundaries where line breaks can occur |
ZWNJ |
U+200C | Zero-Width Non-Joiner | Prevents characters from joining in scripts like Arabic |
ZWJ |
U+200D | Zero-Width Joiner | Joins characters that wouldn't normally connect |
LRM |
U+200E | Left-to-Right Mark | Controls text direction in bidirectional text |
RLM |
U+200F | Right-to-Left Mark | Controls text direction in bidirectional text |
When these invisible characters are arranged in specific patterns, they can represent encoded information. For example, a binary encoding might use Zero-Width Space (ZWSP) to represent "0" and Zero-Width Non-Joiner (ZWNJ) to represent "1" - creating a completely invisible binary representation of your message.
The Encryption Process
- Text to Binary Conversion: Your message is first converted to binary (a series of 0s and 1s)
- Binary to Zero-Width Mapping: Each binary digit is mapped to a specific zero-width character
- Integration with Cover Text: The zero-width characters are inserted between characters of normal "cover" text
- Result: A normal-looking message that contains invisible encoded data
Simplified Example:
Original message: "Secret password"
Binary representation: 01010011 01100101 01100011 01110010 01100101 01110100 00100000 01110000 01100001 01110011 01110011 01110111 01101111 01110010 01100100
Zero-width encoding: [ZWSP][ZWNJ][ZWSP][ZWNJ][ZWSP][ZWSP][ZWNJ][ZWNJ]... (invisible characters)
Cover text: "This is a normal message."
Final result: "T[ZWSP]h[ZWNJ]i[ZWSP]s[ZWNJ] [ZWSP]i[ZWSP]s[ZWNJ] [ZWNJ]a..." (appears as "This is a normal message.")
Advantages of Zero-Width Encryption
Double-Layer Security
Provides a steganographic layer on top of traditional encryption for extra protection.
Plausible Deniability
The very existence of a hidden message is concealed, providing an extra layer of privacy.
Evades Detection
Most scanning and monitoring systems won't recognize that encrypted data is present.
Copy-Paste Compatible
The hidden message remains intact when the text is copied and pasted in most applications.
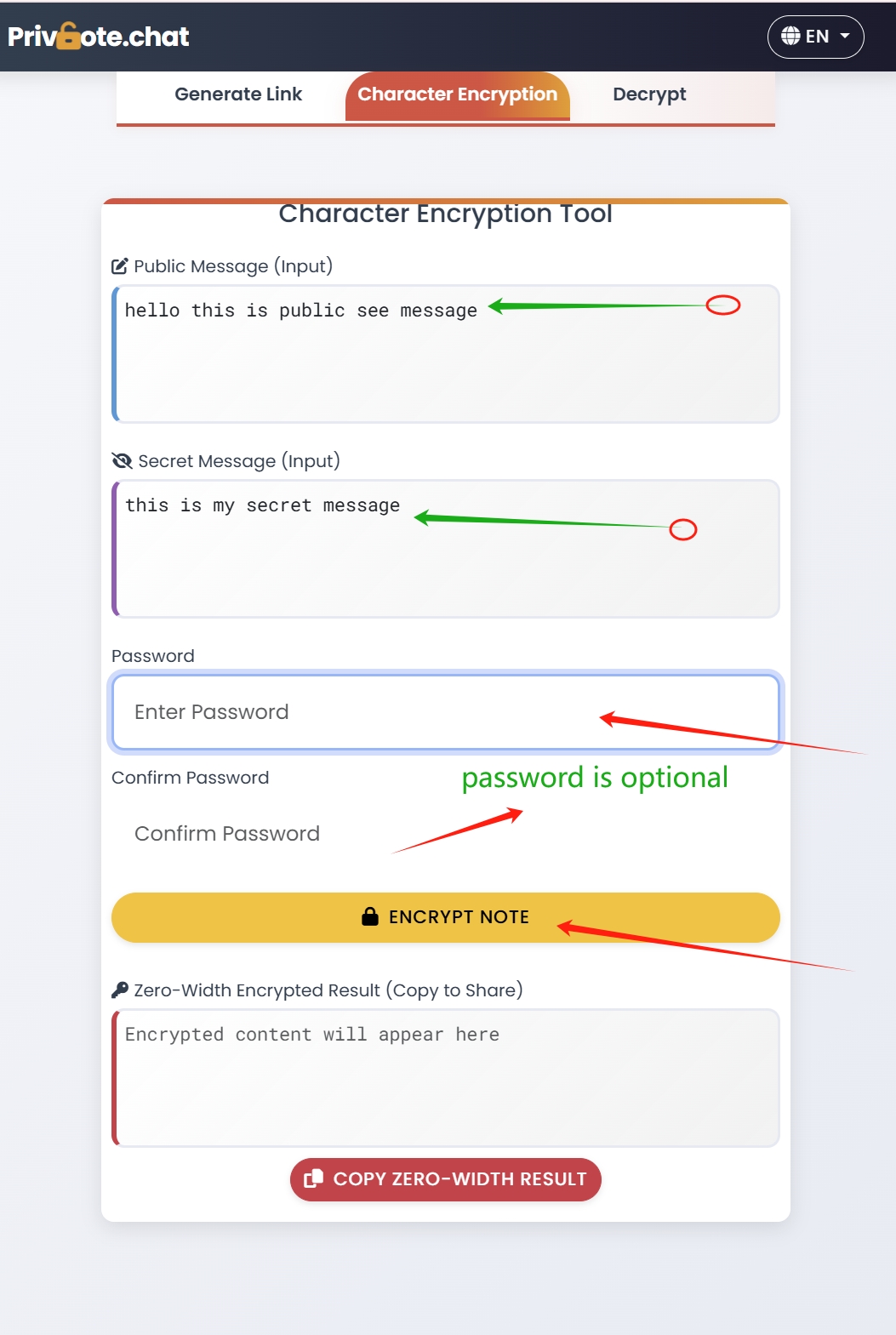
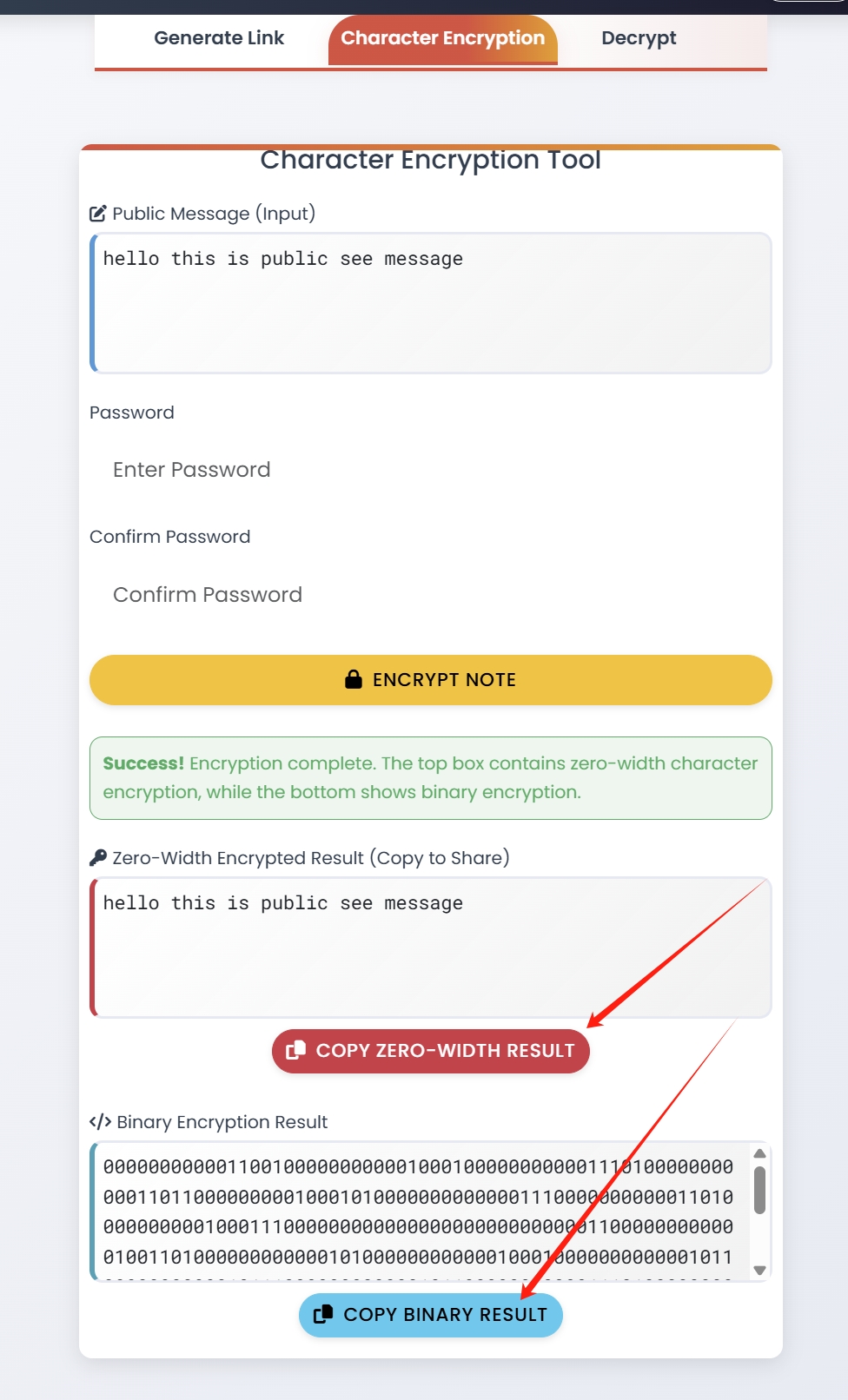
How Privnote Implements Zero-Width Encryption
Privnote takes zero-width character encryption to the next level by combining it with our self-destructing notes technology. Here's how our implementation works:
The Privnote Zero-Width Encryption Process
-
Advanced Encryption
Your message is first encrypted using strong AES-256 encryption
-
Zero-Width Encoding
The encrypted data is then encoded using a proprietary mix of zero-width characters
-
Cover Text Integration
You can choose to hide this data within innocent-looking cover text of your choice
-
Self-Destruction Mechanism
The encoded message is set to self-destruct after being read once
Important:
Zero-width encryption is most effective when the existence of the message itself needs to remain secret. For standard secure communications where only the content needs protection, our regular self-destructing notes provide excellent security with simpler usability.
Real-World Applications
1. Whistleblower Protection
Journalists and whistleblowers can use zero-width encryption to exchange sensitive information in ways that appear completely innocent to monitoring systems. The encrypted data can be hidden in ordinary social media posts, comments, or emails.
2. Covert Business Communications
Companies dealing with highly sensitive intellectual property can use zero-width encryption to transmit confidential information through channels that may be monitored by competitors.
3. Digital Watermarking
Content creators can embed invisible zero-width watermarks in their text-based content to prove ownership in case of plagiarism or unauthorized distribution.
4. Secure Authentication
Zero-width characters can be used as part of sophisticated authentication systems where invisible tokens are embedded in verification messages.
Technical Considerations and Limitations
While zero-width character encryption provides powerful steganographic capabilities, there are some important technical considerations to keep in mind:
Limitations
- Text Editors and Processors: Some text editors may strip or modify zero-width characters
- Format Conversion: Converting between document formats can sometimes remove these special characters
- Sophisticated Detection: Specialized tools can detect the presence of zero-width characters with statistical analysis
- Length Limitations: The ratio of hidden text to visible text creates practical limits on message size
For these reasons, Privnote combines zero-width character encryption with our self-destructing notes technology - ensuring your sensitive information is both well-hidden and temporary.
The Technical Implementation
For those interested in the technical details, here's a simplified example of how zero-width character encryption might be implemented:
// Simplified example of zero-width encoding (not actual Privnote code)
function encodeToZeroWidth(text) {
// Convert text to binary representation
const binaryStr = textToBinary(text);
// Map binary digits to zero-width characters
let zeroWidthEncoded = '';
for (let i = 0; i < binaryStr.length; i++) {
if (binaryStr[i] === '0') {
zeroWidthEncoded += '\u200B'; // Zero-Width Space
} else {
zeroWidthEncoded += '\u200C'; // Zero-Width Non-Joiner
}
}
return zeroWidthEncoded;
}
function hideInCoverText(zeroWidthText, coverText) {
// Insert zero-width characters between visible characters
let result = '';
for (let i = 0; i < coverText.length; i++) {
result += coverText[i];
if (i < zeroWidthText.length) {
result += zeroWidthText[i];
}
}
return result;
}
The decoding process works in reverse, extracting the zero-width characters, mapping them back to binary, and then converting the binary back to text.
Ethical Considerations
As with any powerful security technology, zero-width encryption comes with ethical responsibilities. At Privnote, we believe in responsible use of privacy technologies:
Our Position:
We provide zero-width encryption as a tool for legitimate privacy needs. While we recognize that powerful security tools can be misused, we believe that privacy is a fundamental right and that responsible individuals should have access to strong privacy tools for legitimate purposes.
We encourage users to comply with all applicable laws and regulations when using our encryption technologies, and to consider the ethical implications of their communications.
Conclusion: The Invisible Shield
Zero-width character encryption represents a fascinating evolution in digital privacy - the ability to hide information in plain sight. By combining traditional cryptographic security with steganographic techniques, it provides an additional layer of protection for your most sensitive communications.
While not necessary for everyday secure messaging (where our standard self-destructing notes are more appropriate), zero-width encryption offers specialized protection for situations where even the existence of communication needs to remain confidential.
Ready to experience the power of invisible encryption? Try Privnote's zero-width encryption and discover a new dimension of digital privacy.