Corporate Data Leaks: Prevention Strategies for Businesses in 2025
The Growing Threat of Corporate Data Leaks
In today's hyperconnected business environment, corporate data leaks have emerged as one of the most significant threats to organizational security, reputation, and financial stability. The average cost of a data breach reached $5.2 million in 2024, with larger enterprises facing potential damages exceeding $25 million per incident. Beyond immediate financial impacts, data leaks can result in devastating reputational damage, regulatory penalties, and loss of competitive advantage.
The statistics paint a concerning picture for businesses of all sizes:
- 68% of organizations experienced at least one serious data leak attempt in the past year
- Internal actors were responsible for 34% of all corporate data breaches
- The average time to identify a data breach is 207 days, with another 70 days to contain it
- Over 80% of successful data breaches involved human error or social engineering
As we move through 2025, the threat landscape continues to evolve with increasingly sophisticated attack vectors, making comprehensive data leak prevention more critical than ever for business continuity and success.
Common Sources of Corporate Data Leaks
Understanding the primary sources of data leaks is essential for developing effective prevention strategies. These sources generally fall into four categories:
1. Intentional Internal Threats
Despite significant investments in perimeter security, insider threats remain one of the most challenging aspects of data security:
- Disgruntled employees who deliberately leak sensitive information
- Corporate espionage by employees recruited by competitors
- Financial motivations leading employees to sell valuable data
- Departing employees taking intellectual property to new employers
2. Unintentional Internal Errors
Human error continues to be a leading cause of significant data exposure:
- Misdirected communications sending sensitive information to incorrect recipients
- Improper access controls that expose confidential data to unauthorized personnel
- Misconfigured systems or databases that inadvertently expose sensitive information
- Insecure handling of sensitive documents or information
3. External Attack Vectors
Malicious external actors employ increasingly sophisticated methods to obtain corporate data:
- Phishing and social engineering attacks targeting employees with access to sensitive data
- Network intrusions exploiting technical vulnerabilities
- Supply chain compromises accessing your data through trusted third parties
- Advanced persistent threats (APTs) conducting long-term, sophisticated campaigns
4. Third-Party Exposures
Modern businesses rely heavily on partners and vendors who may have access to sensitive data:
- Vendor security inadequacies exposing shared data
- Cloud service provider misconfigurations or vulnerabilities
- Consultant or contractor data handling practices
- APIs and integrations with insufficient security controls
Comprehensive Data Leak Prevention Strategy
Effective data leak prevention requires a multi-layered approach that addresses technological, procedural, and human factors. Here's a comprehensive framework for businesses seeking to strengthen their defenses:
Data Classification and Management
You can't protect what you don't understand. Begin with a thorough assessment of your data landscape:
Implement Data Discovery and Classification
- Conduct regular data audits to identify and catalog sensitive information
- Develop a classification system (e.g., Public, Internal, Confidential, Restricted)
- Implement automated tools to discover and classify data across your infrastructure
- Map data flows to understand how information moves through your organization
Define Data Handling Procedures
- Establish clear policies for handling each classification of data
- Define retention policies to ensure data isn't kept longer than necessary
- Implement secure data disposal procedures for physical and digital assets
- Create processes for data minimization to limit unnecessary collection
Pro Tip
Start with your most sensitive data categories (e.g., intellectual property, customer PII, financial records) and work outward. This focused approach delivers the highest security ROI.
Technical Controls and Monitoring
Deploy technology solutions designed to prevent, detect, and respond to potential data leaks:
Implement Data Loss Prevention (DLP) Solutions
- Deploy endpoint DLP to monitor and control data transfer at the device level
- Implement network DLP to identify sensitive data in transit
- Use cloud access security brokers (CASBs) to extend DLP to cloud services
- Configure content inspection rules based on your data classification schema
Encryption and Access Controls
- Implement end-to-end encryption for sensitive communications
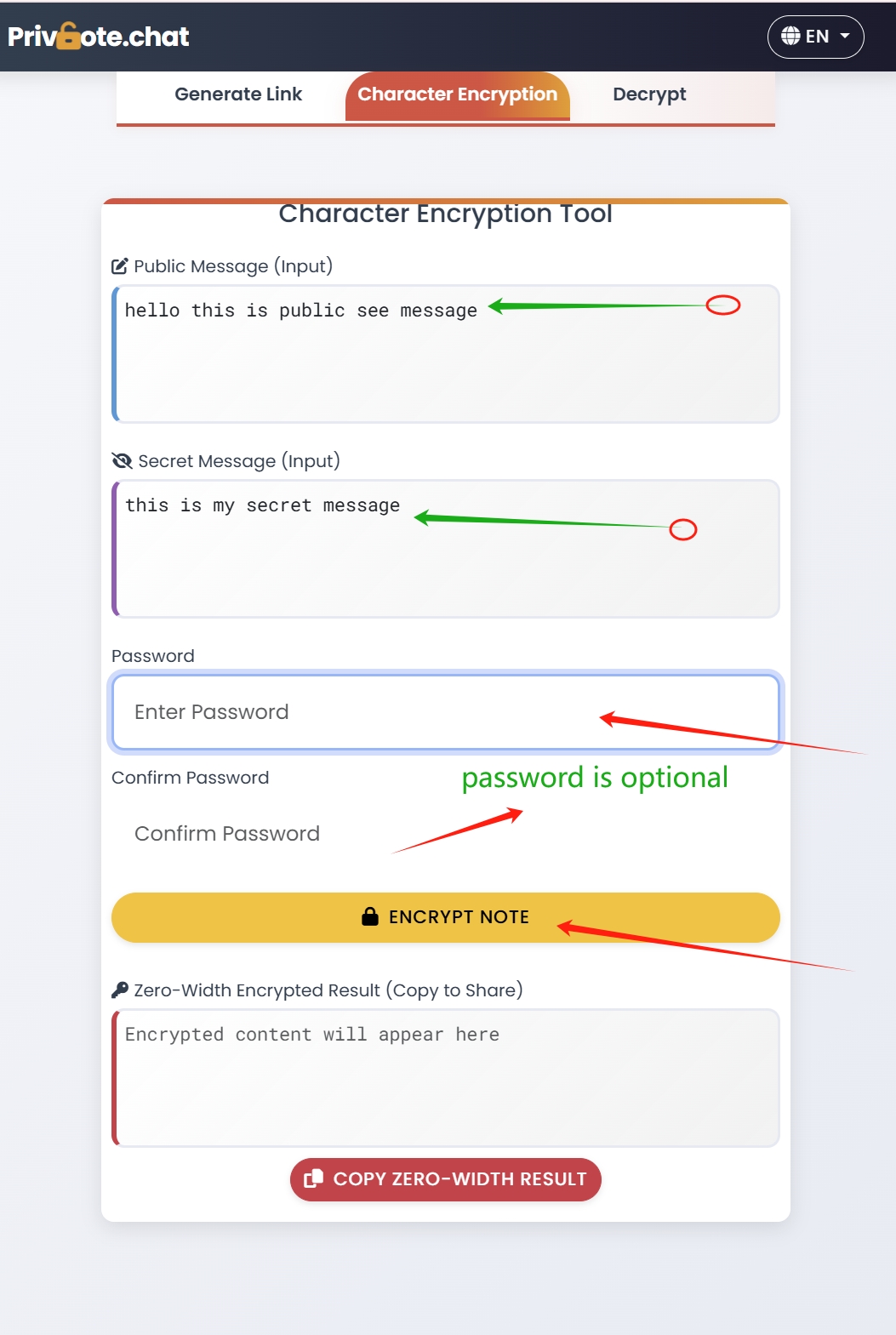
- Use self-destructing message platforms like Privnote for highly sensitive information sharing
- Deploy data-at-rest encryption for stored information
- Implement robust identity and access management (IAM) with least privilege principles
- Require multi-factor authentication for access to sensitive systems and data
Monitoring and Analytics
- Implement user behavior analytics (UBA) to detect anomalous data access patterns
- Deploy security information and event management (SIEM) solutions for comprehensive monitoring
- Establish a security operations center (SOC) or managed detection and response (MDR) capability
- Conduct regular security testing, including red team exercises and penetration tests
People and Process Considerations
Technology alone cannot prevent data leaks. People and processes are equally critical components:
Security Awareness and Training
- Develop role-based security training focused on data handling best practices
- Conduct regular phishing simulations and social engineering assessments
- Create clear guidance on approved communication channels for different sensitivity levels
- Establish a security champion program to embed security awareness throughout the organization
Insider Threat Management
- Implement a comprehensive insider threat program
- Establish clear separation of duties for sensitive functions
- Create secure offboarding procedures to prevent data exfiltration by departing employees
- Develop an anonymous reporting mechanism for potential security concerns
Incident Response Planning
- Develop a detailed data breach response plan
- Establish a cross-functional incident response team
- Conduct regular tabletop exercises and simulations
- Maintain relationships with external forensic and legal resources
- Create communications templates for various breach scenarios
Third-Party Risk Management
Your security is only as strong as your weakest link, which often extends to your business partners:
Vendor Security Assessment
- Implement a formal vendor security assessment process
- Include security requirements in contracts and service level agreements
- Conduct regular security reviews of critical vendors
- Limit vendor access to only the data necessary for their function
Secure Collaboration Tools
- Provide secure tools for external collaboration and file sharing
- Implement data rights management for documents shared externally
- Use ephemeral messaging solutions like Privnote for sharing sensitive information with external parties
- Establish clear guidelines for what information can be shared with third parties
Implementing Ephemeral Communications in Business
One of the most effective strategies for preventing data leaks is to limit the persistence of sensitive information. This is where ephemeral (self-destructing) communications provide significant value for businesses.
Business Use Cases for Self-Destructing Messages
- Sharing access credentials for systems or accounts
- Communicating financial data that shouldn't be permanently stored
- Discussing sensitive HR matters that require documentation minimization
- Transmitting intellectual property with minimized risk of unauthorized access
- Sharing confidential strategic information with select stakeholders
- Communicating temporary access information to contractors or vendors
Best Practices for Ephemeral Business Communications
- Create clear policies specifying which types of information should use ephemeral channels
- Train employees on appropriate use of self-destructing messaging tools
- Document the use of ephemeral communications in your information security policies
- Consider compliance requirements that may necessitate some record retention
- Integrate ephemeral messaging into your formal communications framework
Important Consideration
While ephemeral communications are powerful security tools, they must be balanced with appropriate record-keeping for compliance purposes. Develop clear guidelines about which communications can be ephemeral and which require permanent documentation.
Measuring the Effectiveness of Your Data Leak Prevention
Implementing preventive measures is only the beginning. Organizations must continuously evaluate the effectiveness of their data leak prevention programs:
Key Performance Indicators
- Security incident metrics: Frequency, type, and severity of data-related security incidents
- DLP alert statistics: Volume, false positive rate, and resolution time
- Policy compliance rate: Percentage of users adhering to data handling policies
- Security awareness scores: Results from phishing simulations and security assessments
- Mean time to detect (MTTD): Average time to identify potential data leak incidents
- Mean time to respond (MTTR): Average time to contain and remediate incidents
Continuous Improvement
Data leak prevention should be viewed as an ongoing program rather than a one-time project:
- Conduct regular assessments against industry frameworks (e.g., NIST, ISO 27001)
- Perform periodic red team exercises to test your defenses
- Stay informed about emerging threats and attack vectors
- Regularly update policies and controls based on lessons learned
- Benchmark your program against industry peers and standards
Conclusion: Building a Culture of Data Protection
Ultimately, the most effective defense against corporate data leaks is a comprehensive approach that combines technological controls, robust processes, and a strong security culture. By implementing the strategies outlined in this guide, organizations can significantly reduce their risk of costly and damaging data exposures.
Remember that data leak prevention is not solely an IT responsibility—it requires commitment from leadership, clear policies, appropriate technologies, and engagement from every employee who handles sensitive information.
As the threat landscape continues to evolve, organizations that take a proactive, multi-layered approach to data protection will be best positioned to safeguard their most valuable assets: their data and their reputation.
Looking to enhance your organization's secure communication capabilities? Try Privnote's self-destructing messages as part of your comprehensive data leak prevention strategy.