Secure Collaboration Tools: Why Self-Destructing Notes Should Be Part of Your Toolkit

The Evolution of Collaboration Tools
The modern workplace has undergone a dramatic transformation in recent years, with teams increasingly distributed across different locations and time zones. This shift has driven explosive growth in digital collaboration tools designed to keep teams connected and productive regardless of physical location. According to Gartner, the collaboration software market is projected to reach $50.7 billion by 2025, reflecting the critical importance of these tools in today's work environment.
However, as collaboration tools proliferate, so do the security risks associated with sharing sensitive information across digital channels. Traditional collaboration platforms prioritize persistence and searchability—valuable features for most content, but potentially problematic for sensitive information that shouldn't remain accessible indefinitely.
This is where ephemeral messaging tools like self-destructing notes enter the picture, providing a complementary layer of security for your collaboration toolkit. In this comprehensive guide, we'll explore how combining traditional collaboration tools with ephemeral messaging creates the ideal balance of productivity and security for modern teams.
Market Insight
A 2024 survey by Forrester Research found that 72% of organizations now use at least five different collaboration tools, creating significant challenges for information security teams trying to protect sensitive data across multiple platforms.
The Collaboration Security Challenge
Modern collaboration tools have revolutionized how teams work together, but they've also created new security vulnerabilities that organizations must address:
1. Persistent Information Overload
Traditional collaboration platforms are designed to preserve information indefinitely:
- Chat logs and message histories remain searchable for years
- Shared files persist in cloud storage unless manually deleted
- Email threads containing sensitive information accumulate over time
- Project management tools maintain detailed historical records
While this persistence is valuable for most business information, it creates unnecessary risk for sensitive data that should have a limited lifespan.
2. Oversharing and Access Control Complexity
The ease of sharing in modern collaboration tools can lead to security issues:
- Sensitive information inadvertently shared with too broad an audience
- Complex permission systems that are difficult to manage correctly
- Lack of granular control over information lifespan
- Challenges tracking who has accessed sensitive information
3. Tool Proliferation and Shadow IT
The multiplication of collaboration tools creates security gaps:
- Inconsistent security controls across different platforms
- Employees using unauthorized tools for convenience
- Difficulty tracking where sensitive information resides
- Incomplete security coverage across the collaboration ecosystem
Security Risk:
According to a 2024 study by the Ponemon Institute, 65% of data breaches involving collaboration tools were attributed to excessive persistence of sensitive information that should have been deleted but remained accessible in message histories, shared folders, or email threads.
The Essential Collaboration Toolkit
A comprehensive, security-conscious collaboration strategy requires multiple tools, each serving specific communication needs:
| Tool Category | Primary Purpose | Security Considerations |
|---|---|---|
| Team Messaging Platforms (Slack, Microsoft Teams) |
Ongoing team conversations, quick questions, informal updates | Message persistence, broad visibility, limited ephemerality options |
| Video Conferencing (Zoom, Google Meet) |
Real-time meetings, presentations, visual collaboration | Recording storage, screen sharing risks, meeting access control |
| Document Collaboration (Google Docs, Office 365) |
Co-creating content, formal documentation, persistent records | Version history, access permissions, persistent storage |
| Project Management (Asana, Trello, Jira) |
Task tracking, project coordination, workflow management | Extensive audit trails, task visibility, persistent documentation |
| Self-Destructing Notes (Privnote) |
Sharing sensitive, temporary information securely | Automatic deletion, access controls, minimal persistence |
The Role of Self-Destructing Notes in Modern Collaboration
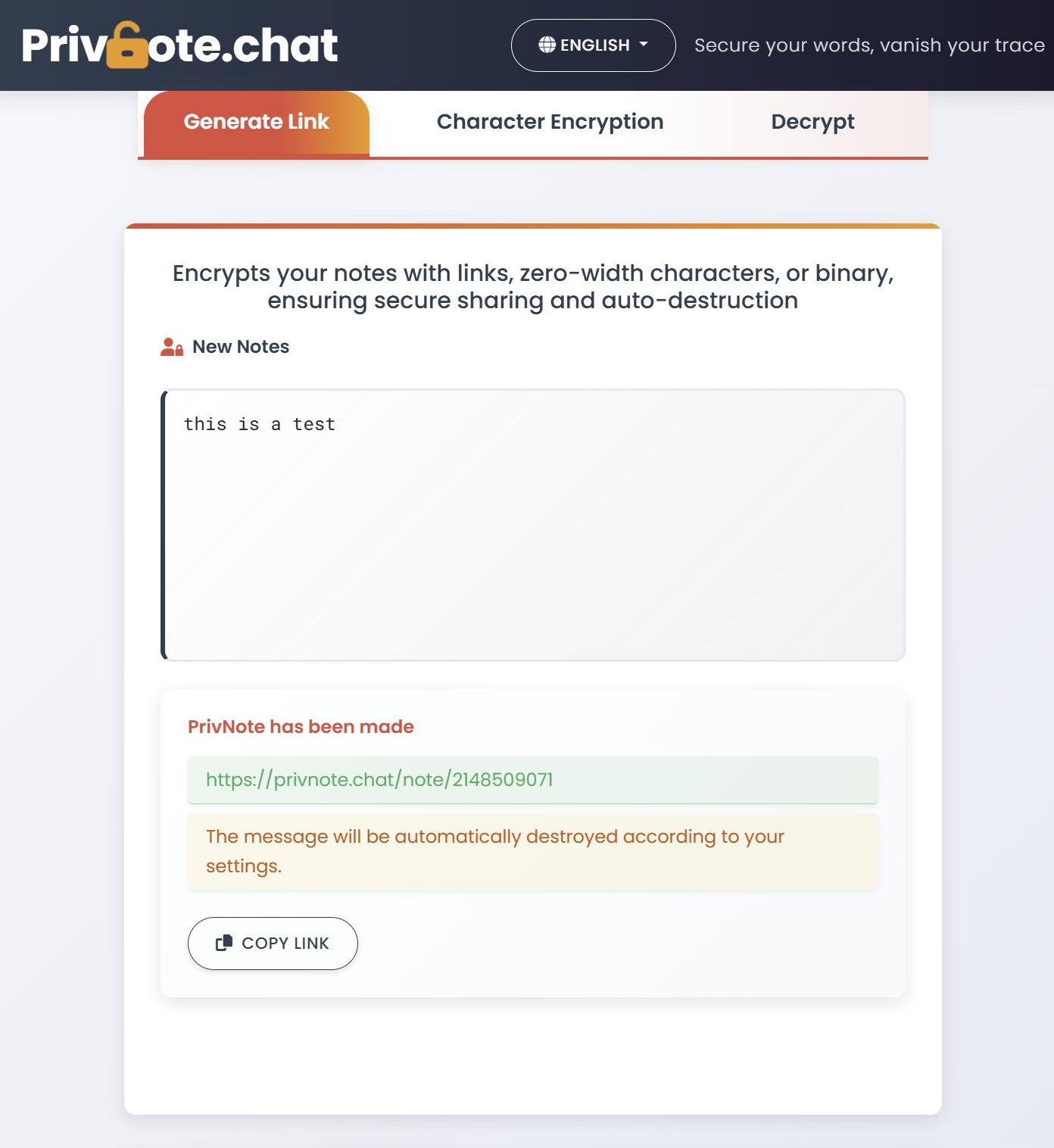
Self-destructing notes fill a critical gap in the collaboration toolkit by providing secure, ephemeral messaging capabilities. Here's how they complement traditional collaboration tools:
1. Sensitive Information Layer
Self-destructing notes create a dedicated channel for your most sensitive communications:
- Information segregation: Keep sensitive data separate from general collaboration channels
- Purpose-specific sharing: Use the right tool for different information sensitivity levels
- Reduced data liability: Minimize the amount of sensitive information persisting in your systems
Security Benefit
By using self-destructing notes for sensitive information sharing, you create a clear distinction between persistent business records (stored in traditional collaboration tools) and ephemeral sensitive communications (shared via self-destructing notes).
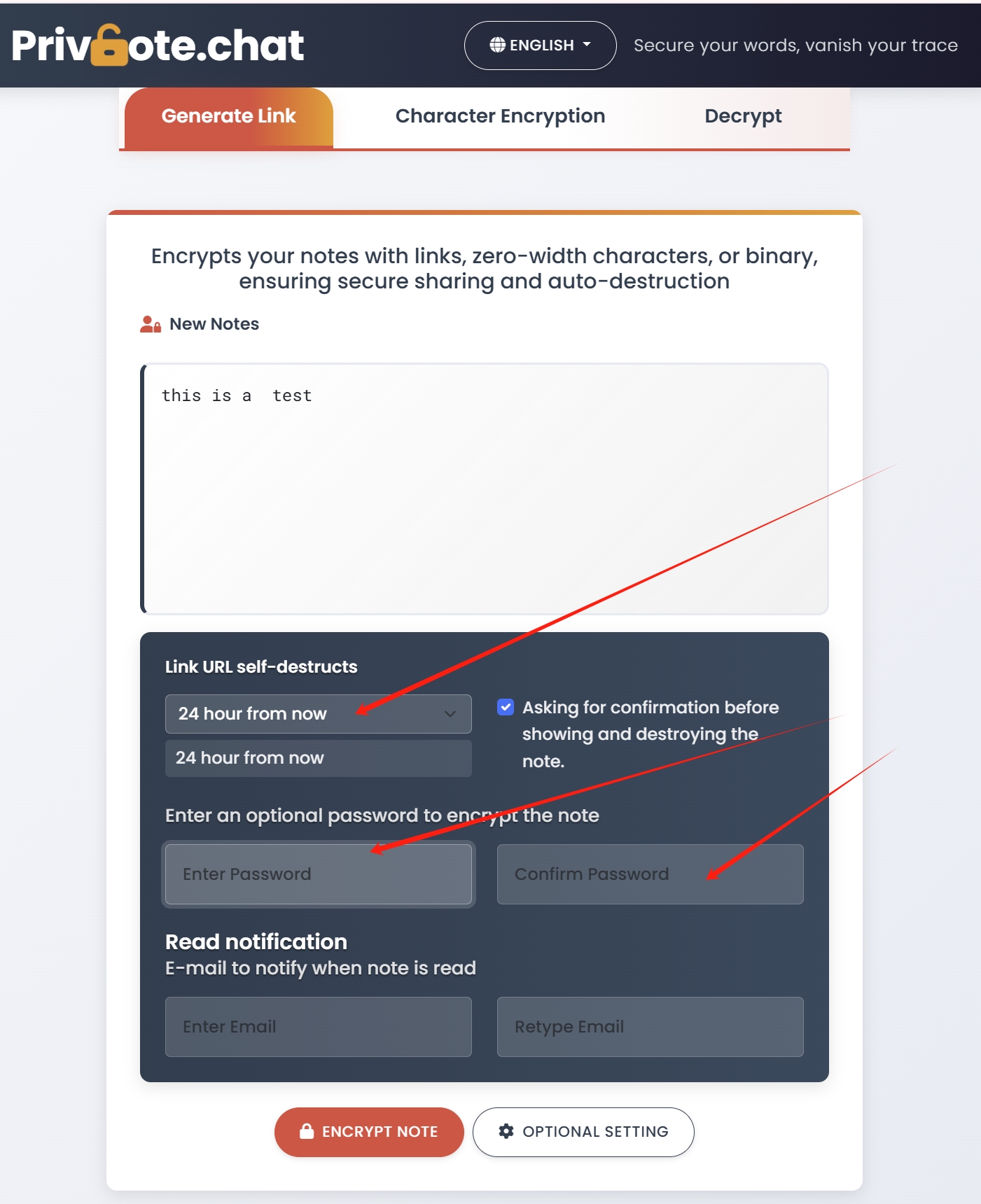
2. Precision Access Control
Self-destructing notes offer granular control over information access:
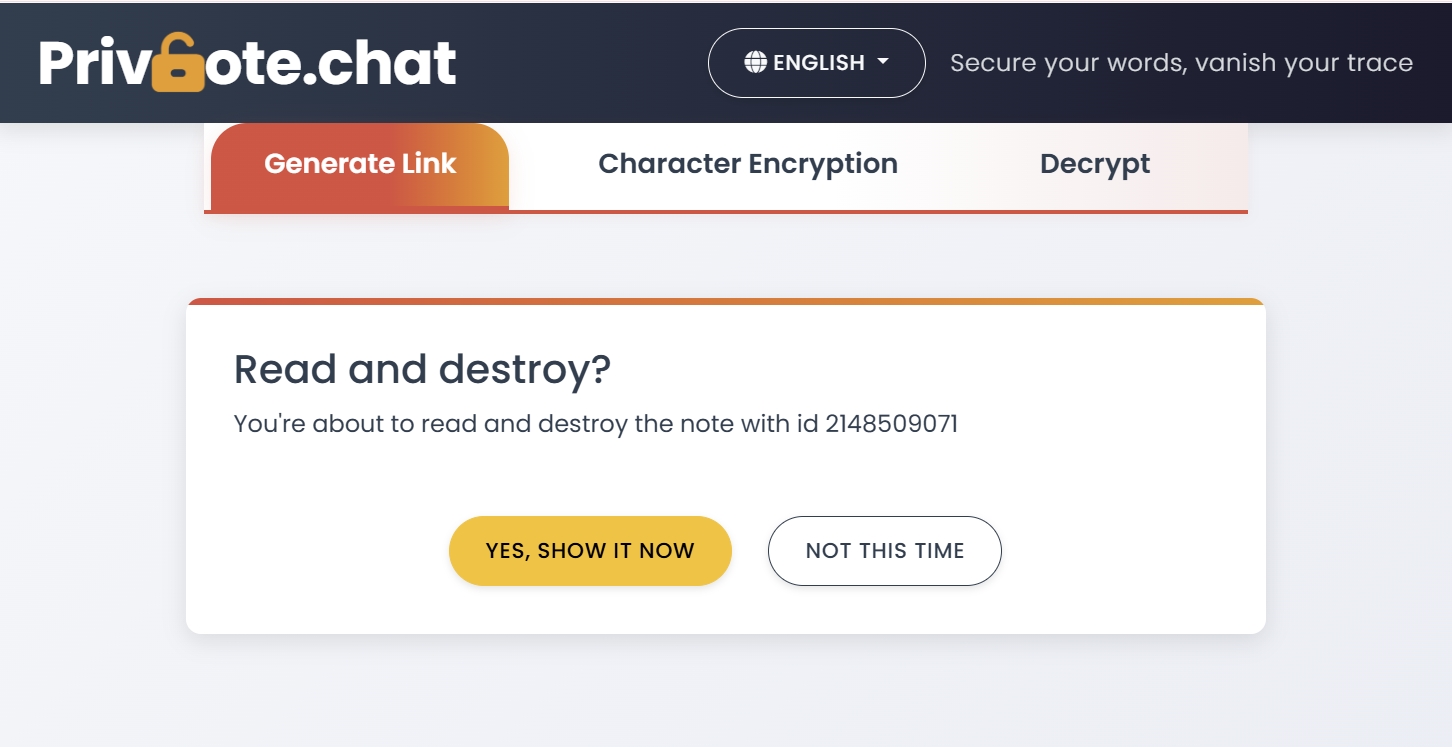
- One-time access: Information viewable only once before automatic deletion
- Password protection: Additional verification layer for sensitive content
- Temporal control: Custom expiration settings for time-limited access
- Read confirmation: Verification that information was received
3. Cross-Platform Compatibility
Self-destructing notes work seamlessly across your collaboration ecosystem:
- Platform-agnostic: Share secure links through any communication channel
- No software installation: Recipients need only a web browser to access
- Consistent security: Same protection regardless of recipient's environment
- External sharing: Secure communication with partners outside your organization
Key Use Cases for Self-Destructing Notes in Collaborative Environments
Here are practical scenarios where self-destructing notes enhance team collaboration security:
1. Credential and Access Sharing
Implementation Strategy:
When team members need temporary access to systems or resources:
- Create a self-destructing note containing the necessary credentials
- Enable password protection for dual-factor security
- Share the note link through your team messaging platform
- Provide the password through a different channel
- Set appropriate expiration timing based on access needs
Benefits: Credentials don't persist in chat logs or email, access information automatically disappears after use, and you receive confirmation when credentials have been viewed.
2. Sensitive Project Information
For confidential project details that shouldn't be broadly documented:
- Preliminary budget discussions before formal approval
- Early-stage strategic planning information
- Confidential client requirements or feedback
- Sensitive competitive analysis or market insights
Business Example
A product team working on an unannounced feature can use self-destructing notes to share sensitive development details that shouldn't be documented permanently in project management tools until the feature is officially approved.
3. HR and Personnel Matters
Human resources teams handle particularly sensitive information:
- Preliminary compensation discussions
- Performance review preparation notes
- Sensitive employee relations matters
- Organizational restructuring planning
4. Security Incident Coordination
During security incidents, self-destructing notes provide secure communication:
- Sharing details about vulnerabilities being investigated
- Coordinating incident response across teams
- Providing temporary access to incident response resources
- Communicating sensitive findings before official reporting
5. Third-Party Collaboration
When working with external partners and vendors:
- Sharing time-limited access information
- Providing confidential specifications or requirements
- Exchanging sensitive contract details during negotiation
- Temporary access to restricted project information
Implementing Self-Destructing Notes in Your Collaboration Workflow
To successfully integrate ephemeral messaging into your collaboration strategy, follow these implementation best practices:
1. Create Clear Usage Guidelines
Establish policies for when different collaboration tools should be used:
Information Classification Framework
- Permanent Business Records: Document collaboration platforms, project management tools
- General Team Communication: Team messaging platforms, email
- Sensitive Temporary Information: Self-destructing notes
- Highly Confidential Information: Self-destructing notes with password protection
2. Integrate with Existing Tools
Make self-destructing notes work seamlessly with your current collaboration stack:
- Share self-destructing note links through your primary team messaging platform
- Create shortcuts or bookmarks for quick access to your ephemeral messaging tool
- Document the role of self-destructing notes in your communication guidelines
- Consider integration possibilities through APIs or workflows when available
3. Provide Comprehensive Training
Ensure team members understand when and how to use different collaboration tools:
- Include self-destructing notes in your collaboration tools training
- Provide clear examples of appropriate use cases
- Explain the security benefits and limitations
- Create simple decision trees for selecting the right communication channel
Important Consideration
Make it clear that self-destructing notes complement rather than replace proper document management. Information that requires permanent storage for business, legal, or compliance reasons should still be properly documented in appropriate systems.
4. Implement Security Best Practices
Maximize the security benefits of your ephemeral messaging:
Multi-Channel Authentication
Send self-destructing note links through one channel and passwords through another for maximum security.
Appropriate Timing
Set reasonable expiration times that balance security with the recipient's need for access.
Verification Features
Use read receipts to confirm when team members have accessed important information.
Enhanced Encryption
For highly sensitive information, use advanced encryption options like zero-width character encryption.
5. Monitor and Adjust
Continuously improve your collaboration security strategy:
- Gather feedback on the usability and effectiveness of your ephemeral messaging solution
- Track adoption rates and identify barriers to implementation
- Adjust policies based on real-world usage patterns
- Stay informed about new features and security enhancements
Comparing Ephemeral Messaging Options
While self-destructing notes are essential for secure collaboration, it's important to understand the different options available:
| Feature | Privnote Self-Destructing Notes | Disappearing Messages in Messaging Apps | Enterprise Ephemeral Messaging |
|---|---|---|---|
| Account Requirements | No accounts needed | Both parties need accounts | Enterprise accounts required |
| Accessibility | Works in any web browser | Requires specific app installation | Often requires specific software |
| External Sharing | Easy sharing with anyone | Limited to platform users | Often restricted to organization |
| Additional Security | Password protection, custom expiration | Varies by platform | Advanced but complex controls |
| Ideal Use Case | Cross-platform sensitive information sharing | Ongoing team chats with some sensitive content | High-regulation industries with strict compliance |
Conclusion: A Balanced Approach to Secure Collaboration
Effective collaboration in today's digital workplace requires a thoughtful balance between security and productivity. While traditional collaboration tools excel at facilitating teamwork and preserving institutional knowledge, they often lack the specialized security features needed for truly sensitive information.
By adding self-destructing notes to your collaboration toolkit, you create a dedicated channel for ephemeral, sensitive communications—enhancing your overall security posture without sacrificing the benefits of your existing collaboration platforms.
The key to success lies in clear policies, proper training, and thoughtful integration of ephemeral messaging into your broader collaboration strategy. When team members understand which tool to use for different types of information, they can collaborate efficiently while maintaining appropriate security for sensitive data.
Ready to enhance your team's collaboration security? Try Privnote's self-destructing notes as part of your secure collaboration toolkit.