Secure Password Sharing: Best Practices and Tools in 2025
The Password Sharing Dilemma
We all know we shouldn't share passwords. Every cybersecurity expert, IT professional, and digital privacy advocate emphasizes the importance of keeping your credentials private. Yet, the reality is that password sharing happens daily in both personal and professional contexts:
- IT administrators need to provide temporary access to systems
- Family members share streaming service credentials
- Teams collaborate on shared accounts for business tools
- Friends provide Wi-Fi passwords to guests
When these inevitable situations arise, the question becomes not if you should share a password, but how to do so securely. This guide explores the safest methods for sharing passwords in 2025, with a focus on self-destructing notes technology that minimizes risk.
Common Password Sharing Mistakes to Avoid
1. Sending Passwords via Regular Email
Standard email is one of the riskiest channels for password sharing. Emails are:
- Stored indefinitely on multiple servers
- Often backed up automatically
- Vulnerable to account breaches
- Typically unencrypted during transmission
A password sent via email can potentially remain accessible for years, creating a permanent security vulnerability.
2. Using Standard Messaging Apps
Popular messaging platforms like WhatsApp, Facebook Messenger, and SMS texts present similar problems:
- Messages may be backed up to cloud storage
- Conversations often sync across multiple devices
- Recipients may take screenshots
- Some platforms analyze message content
3. Sharing Through Documents or Notes
Shared documents, spreadsheets, or note-taking apps are especially problematic for password storage:
- Access permissions can be difficult to manage over time
- Documents often persist long after they're needed
- Revision history may preserve deleted passwords
- Cloud storage increases exposure risk
Secure Password Sharing with Self-Destructing Notes
Self-destructing notes technology offers the ideal solution for secure password sharing. Services like Privnote create temporary, encrypted messages that automatically delete themselves after being read once. This approach addresses the key security concerns of password sharing:
1. Automatic Deletion
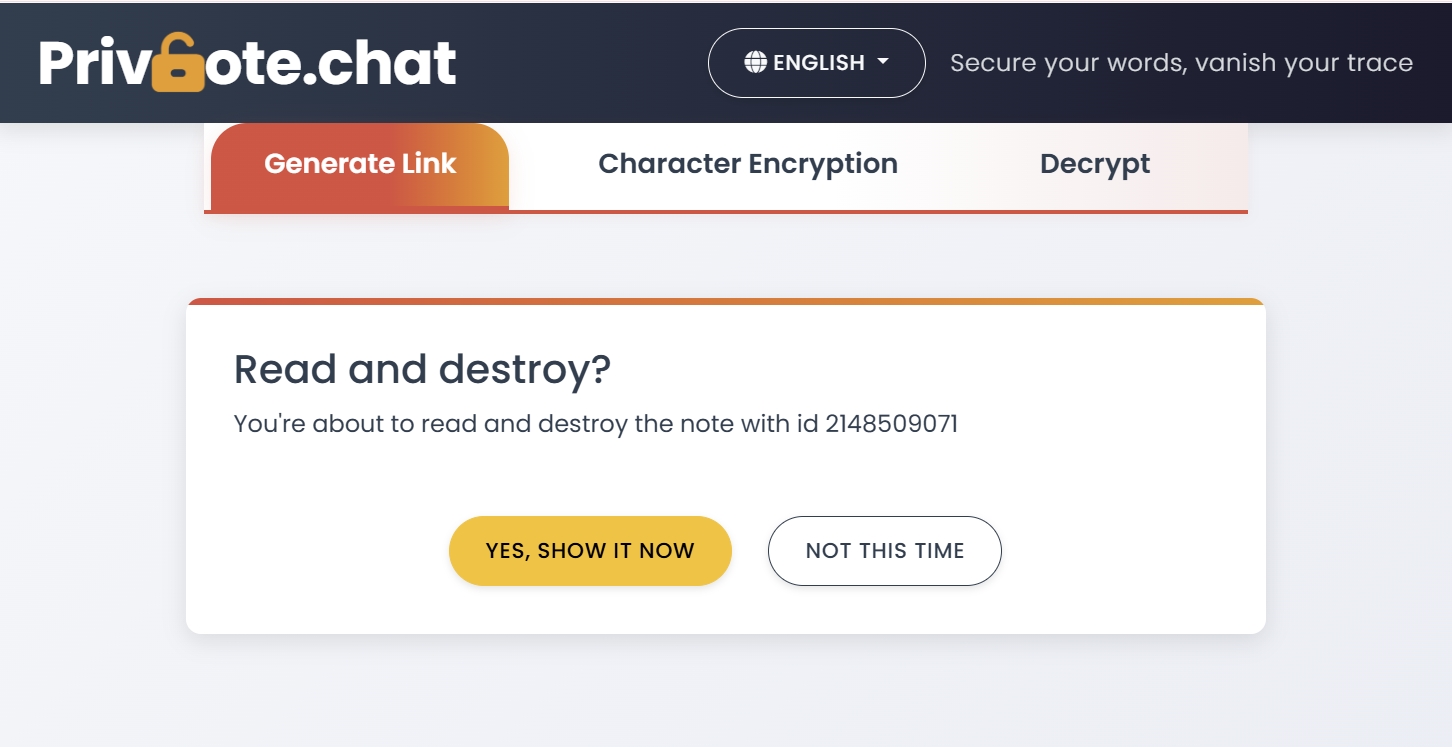
The primary advantage of self-destructing notes is that they eliminate the lingering digital footprint of shared passwords. Once the recipient views the password, the note is permanently deleted from all servers—there's nothing left to find, hack, or leak.
2. One-Time Access
Each self-destructing note can only be accessed once. This ensures that the link becomes invalid after the intended recipient views it, preventing unauthorized access through leaked or stolen links.
3. Additional Security Layers
Advanced self-destructing note services offer extra security features:
- Password Protection: Require a second password to open the note
- Timed Expiration: Set notes to expire after a certain period even if unopened
- Read Notifications: Receive alerts when your note is accessed
- Reference Codes: Use partial information that only makes sense with pre-shared context
Step-by-Step Guide to Secure Password Sharing
Here's a comprehensive process for sharing passwords securely using self-destructing notes technology:
Step 1: Prepare Your Password Information
Before creating your secure note, gather all necessary information:
- The username and password
- The specific service or website the credentials are for
- Any additional authentication information (security questions, backup codes)
- Instructions for use, if necessary
- The expiration date of the shared access (if applicable)
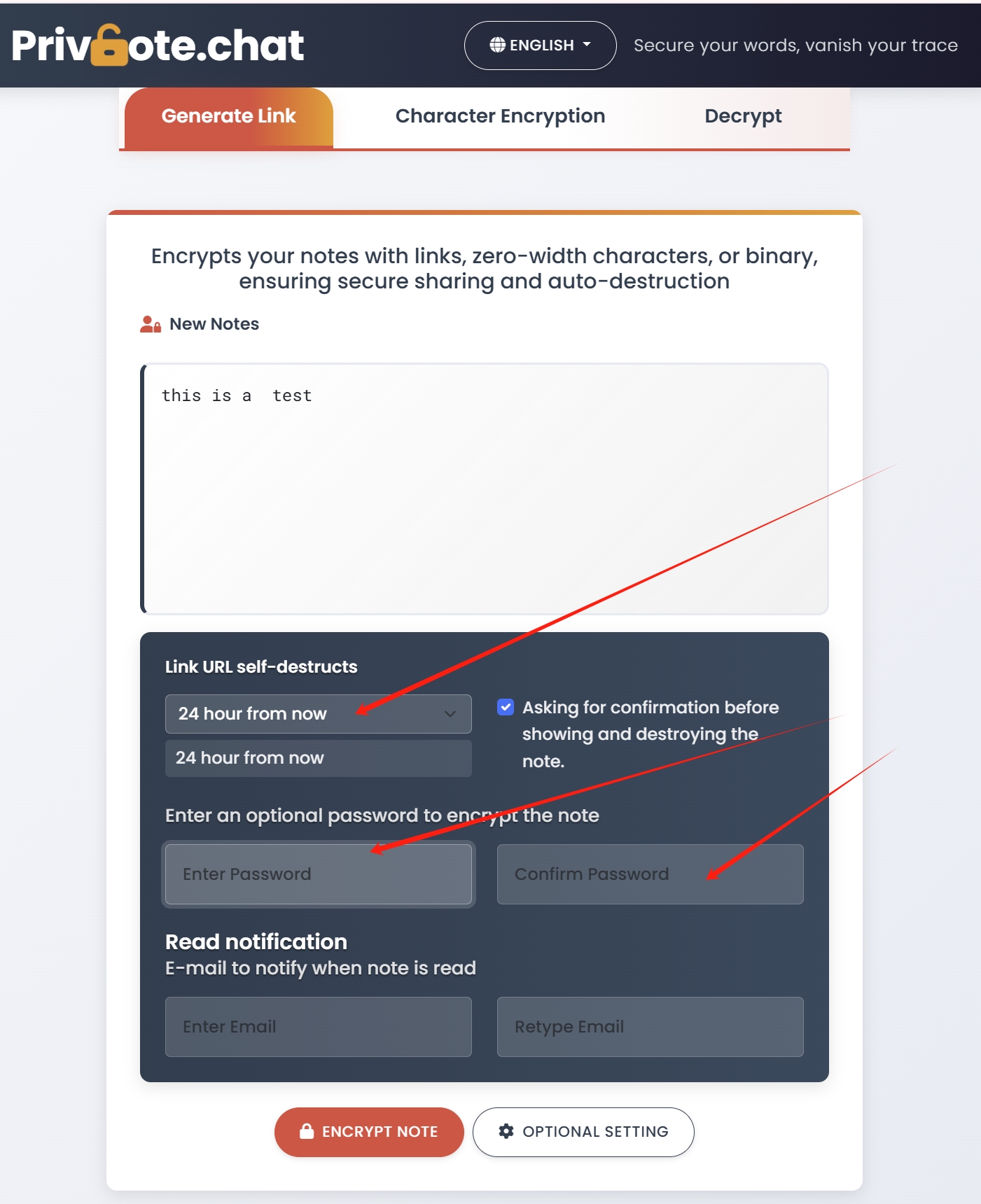
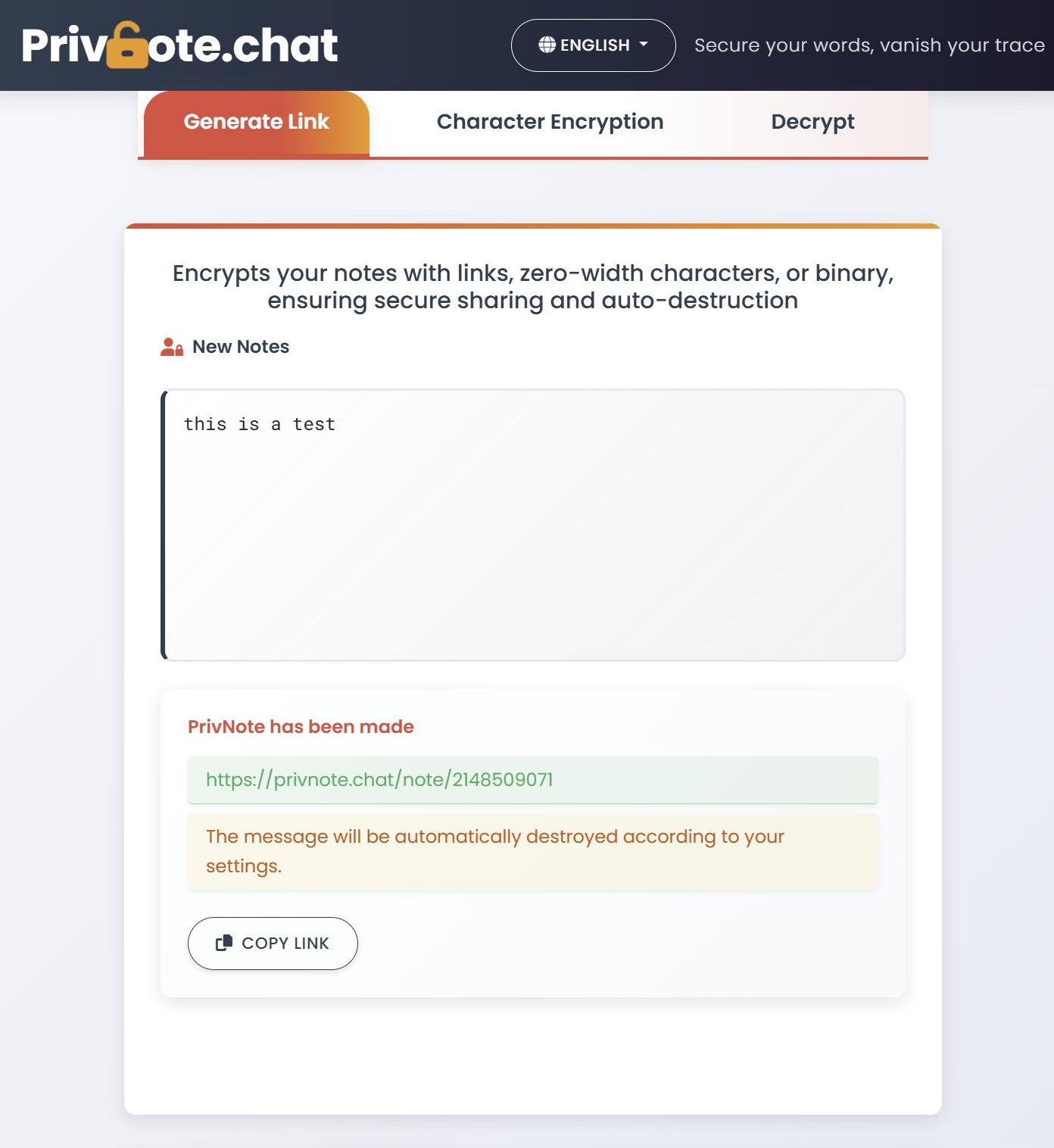
Step 2: Create a Self-Destructing Note
- Visit a secure self-destructing note service like Privnote
- Type or paste your password information
- Configure security options (password protection, expiration time)
- Generate the secure, one-time link
Step 3: Share the Link Securely
Send the link to your recipient through a different channel than your regular communications:
- If you normally communicate by email, send the link via a messaging app
- If you usually use messaging apps, consider a phone call or SMS
- For high-security situations, split the information across multiple channels
Step 4: Follow Up Securely
After sharing:
- Confirm the recipient successfully accessed the information
- Remind them not to store the password insecurely
- Consider changing the password after the shared access period ends
Advanced Techniques for High-Security Situations
Split Delivery Method
For extremely sensitive credentials, consider splitting the password information:
- Send the username through one channel
- Send the password through a self-destructing note
- Send any 2FA or additional authentication details through a third channel
This ensures that even if one communication channel is compromised, the complete access information remains secure.
Reference Code System
Create a system where your self-destructing note contains only part of the necessary information:
- Pre-share a pattern or template with trusted individuals
- In your secure note, include only the unique elements that complete the pattern
- This provides an additional layer of security if the link falls into the wrong hands
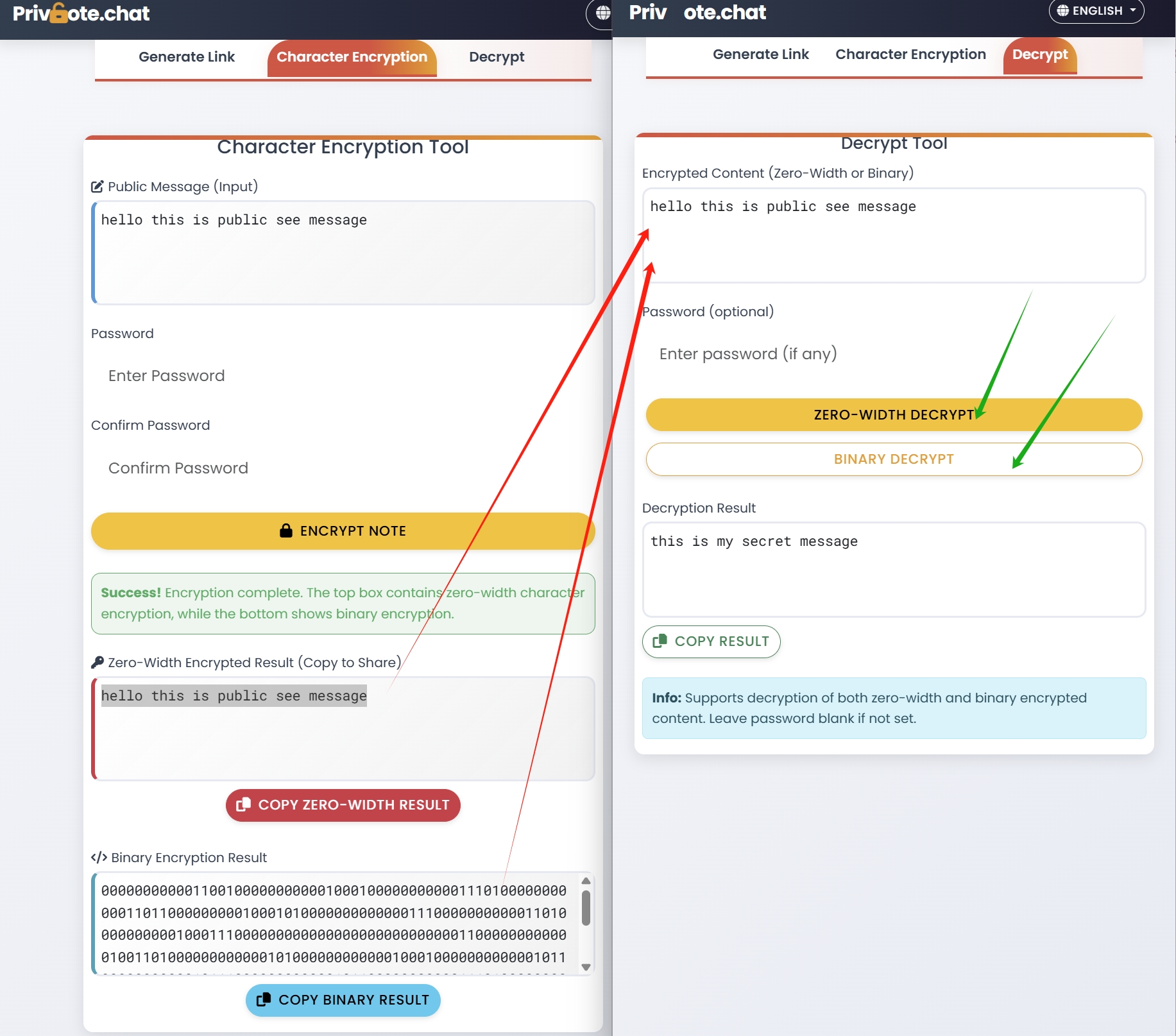
Zero-Width Character Encryption
For the highest level of security, consider using zero-width character encryption within your self-destructing note:
- This hides your password within seemingly normal text
- Creates two layers of security (the self-destructing note and the hidden message)
- Provides protection even if someone intercepts the note access
Learn more about this technique in our guide to zero-width character encryption.
Password Sharing in Specific Contexts
Family Password Sharing
Families often need to share passwords for household accounts, streaming services, and emergency access:
- Use self-destructing notes when initially sharing credentials
- Consider a secure password manager for ongoing family access
- Create separate user accounts when possible instead of sharing credentials
- Establish clear rules about which family passwords can be shared with others
Business and Team Password Sharing
In professional environments, secure password sharing is even more critical:
- Use self-destructing notes for one-time or temporary access needs
- Implement role-based access controls where possible
- Maintain detailed logs of who has access to which credentials
- Regularly rotate passwords for shared accounts
- Train team members on secure password handling procedures
IT Administrative Access
System administrators often need to share temporary privileged access:
- Use self-destructing notes with short expiration times
- Create temporary credentials rather than sharing permanent ones
- Implement just-in-time access protocols
- Maintain detailed access logs
- Reset passwords immediately after temporary access periods
Conclusion: A Balanced Approach to Password Sharing
While the ideal security practice remains "never share passwords," the reality of our interconnected digital lives sometimes requires exceptions. When those situations arise, self-destructing notes provide the most secure method for sharing sensitive credentials.
By following the best practices outlined in this guide and leveraging Privnote's secure, ephemeral messaging technology, you can minimize the risks associated with password sharing while still enabling necessary collaboration and access.
Remember, the goal isn't just to share a password—it's to share access temporarily while maintaining long-term security. Self-destructing notes make this delicate balance possible.
Ready to share passwords securely? Try Privnote's self-destructing notes for your next credential sharing need.