Messaging Security 101: A Beginner's Guide to Secure Communication
Why Secure Messaging Matters
In today's digital world, we share our most personal thoughts, sensitive information, and private details through digital messages. From casual conversations with friends to confidential work discussions and financial information, our messages contain fragments of our lives that we often don't want publicly exposed.
Yet standard messaging is surprisingly vulnerable:
- Messages can be stored indefinitely on multiple servers
- Unencrypted messages can be intercepted during transmission
- Service providers may have access to your message content
- Account breaches can expose years of conversation history
- Even deleted messages often remain in backups or recipient devices
Secure messaging addresses these vulnerabilities by implementing various protective measures to keep your communications private. This guide will walk you through the basics of messaging security, helping you understand the key concepts and make informed choices about your digital conversations.
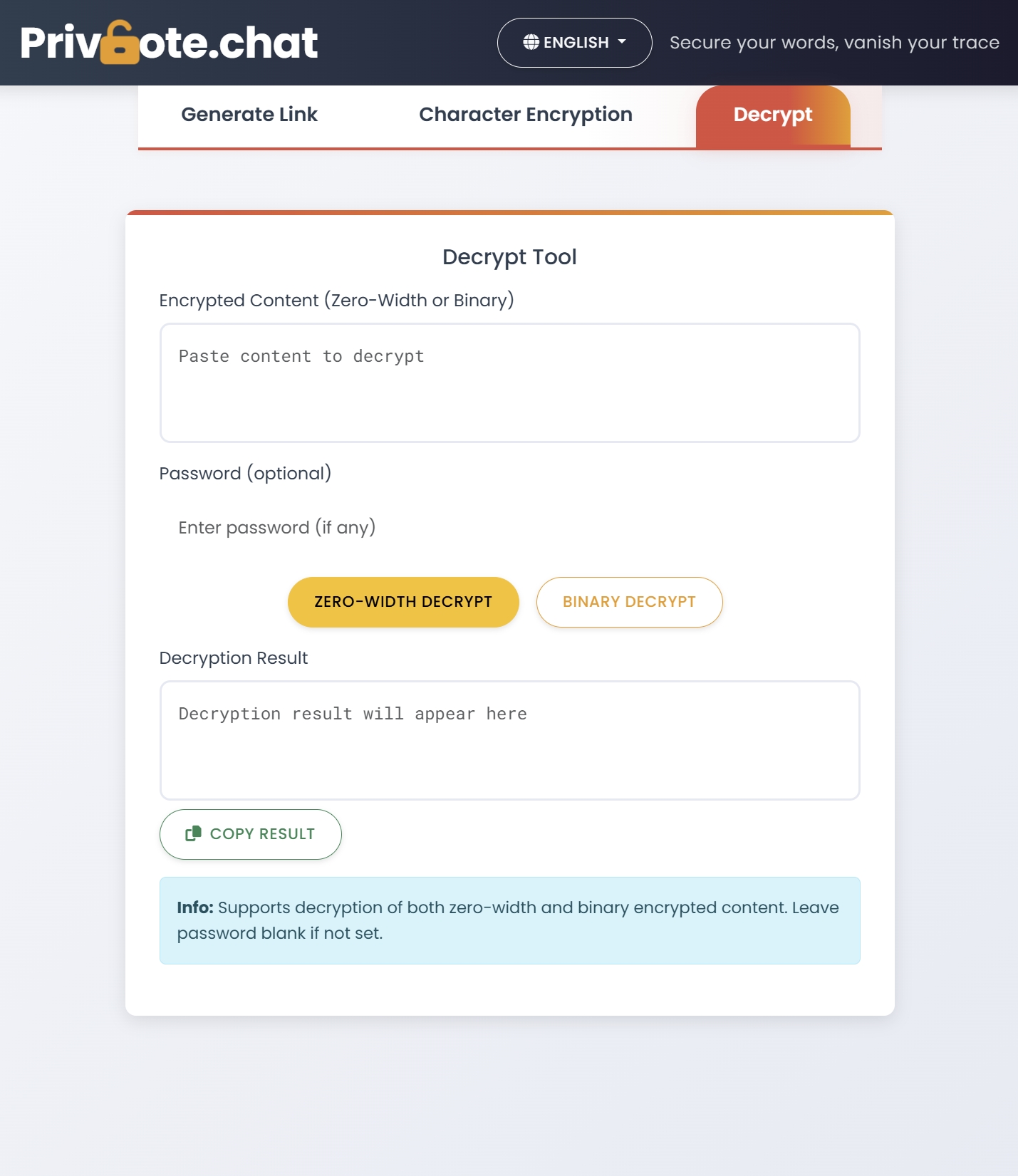
How Privnote Works: Secure Message Flow
Before diving into encryption details, let's understand how a secure messaging service like Privnote ensures your messages remain private. The following diagram illustrates the complete flow from creating a message to its automatic destruction:
As you can see from the diagram, Privnote implements multiple security layers: client-side encryption, secure storage of only encrypted data, and immediate destruction after the message is read. This ensures that even if someone intercepts the link or accesses the server, they cannot read your sensitive information.
Understanding Encryption: The Foundation of Secure Messaging
At the heart of secure messaging is encryption—the process of converting readable information (plaintext) into scrambled code (ciphertext) that can only be decoded with the right key. Think of it as putting your message in a lockbox where only the intended recipient has the key.
Types of Encryption in Messaging
Transport Encryption
This protects messages while they're traveling between your device and the service provider's servers. Almost all modern messaging apps use transport encryption (usually TLS/SSL), but this alone isn't enough for truly secure messaging because:
- Your messages are encrypted only during transmission
- They are decrypted and readable on the service provider's servers
- The provider can access your message content
End-to-End Encryption (E2EE)
This higher level of protection encrypts messages on your device and only decrypts them on the recipient's device. With proper E2EE:
- Even the service provider can't read your messages
- Messages remain encrypted on all servers
- Only you and your recipient hold the decryption keys
Zero-Knowledge Encryption
This advanced approach ensures that only you have the keys to your data:
- Encryption keys are generated from your password
- The service provider never has access to your unencrypted data or keys
- Usually combined with E2EE for maximum security
Specialized Encryption Methods
Some secure messaging platforms offer unique encryption approaches for specialized security needs:
- Zero-Width Character Encryption: Hides messages within seemingly normal text using invisible characters
- Binary Encryption: Converts messages into binary code that requires specific tools to decode
Beginner's Tip
When choosing a messaging app or service, look for the phrase "end-to-end encryption" in their security features. This is the minimum standard for truly secure messaging.
Beyond Encryption: Other Important Security Features
While encryption is crucial, truly secure messaging involves several other important features:
Message Persistence
How long do your messages exist? Options include:
- Permanent messages: Standard in most messaging apps, these persist indefinitely
- Self-destructing messages: Automatically delete after being read or after a set time
- Message expiration: Allow you to set a timeframe after which messages disappear
Metadata Protection
Metadata is information about your messages—who you talk to, when, how often, etc. This can reveal a lot even if the message content is encrypted. Secure messaging should minimize:
- Connection logs
- IP address storage
- Contact relationships
- Message timing records
Authentication
How can you be sure you're actually communicating with the intended person? Secure messaging platforms implement:
- Identity verification methods
- Safety numbers or security codes
- Warning systems for changes in recipient devices
Forward Secrecy
This advanced feature ensures that if your encryption keys are ever compromised in the future, they can't be used to decrypt past messages. This provides protection against:
- Future key compromises
- "Collect now, decrypt later" attacks
- Long-term surveillance risks
Common Security Risks in Messaging
Understanding the potential vulnerabilities helps you make better security choices:
Account Access Risks
- Weak passwords: Easy-to-guess passwords can compromise your entire message history
- Lack of two-factor authentication: Relying solely on passwords increases vulnerability
- Device theft: Physical access to your unlocked device gives access to your messages
Message Interception Risks
- Unencrypted transmission: Messages sent without encryption can be intercepted
- Man-in-the-middle attacks: Attackers positioning themselves between you and your recipient
- Compromised servers: If service providers can read messages, server breaches expose your communications
Endpoint Security Risks
- Device malware: Spyware on your device can capture messages before/after encryption
- Screen capture: Recipients can save screenshots of messages meant to be temporary
- Backup vulnerabilities: Automatic backups may store messages you thought were deleted
Important Note
Even the most secure messaging system can be compromised if either your device or your recipient's device is compromised. Always keep your devices updated and protected with security software.
Types of Secure Messaging Solutions
Different secure messaging options serve different needs:
Secure Messaging Apps
Dedicated apps focused on privacy and security (e.g., Signal, Wickr):
- Pros: Comprehensive security, user-friendly interfaces, support for ongoing conversations
- Cons: Require app installation, both parties need accounts, may collect some metadata
- Best for: Regular secure communications with the same people
Self-Destructing Note Services
Web-based platforms for one-time secure sharing (e.g., Privnote):
- Pros: No accounts needed, true one-time access, cross-platform, minimal data retention
- Cons: Generally text-only, not designed for ongoing conversations
- Best for: Sharing sensitive information one time, especially with people you don't regularly message
Encrypted Email Services
Email providers with enhanced security features (e.g., ProtonMail, Tutanota):
- Pros: Familiar email format, often work with standard email addresses
- Cons: Email headers still contain metadata, variable security depending on recipient
- Best for: More secure alternatives to standard email for less time-sensitive communications
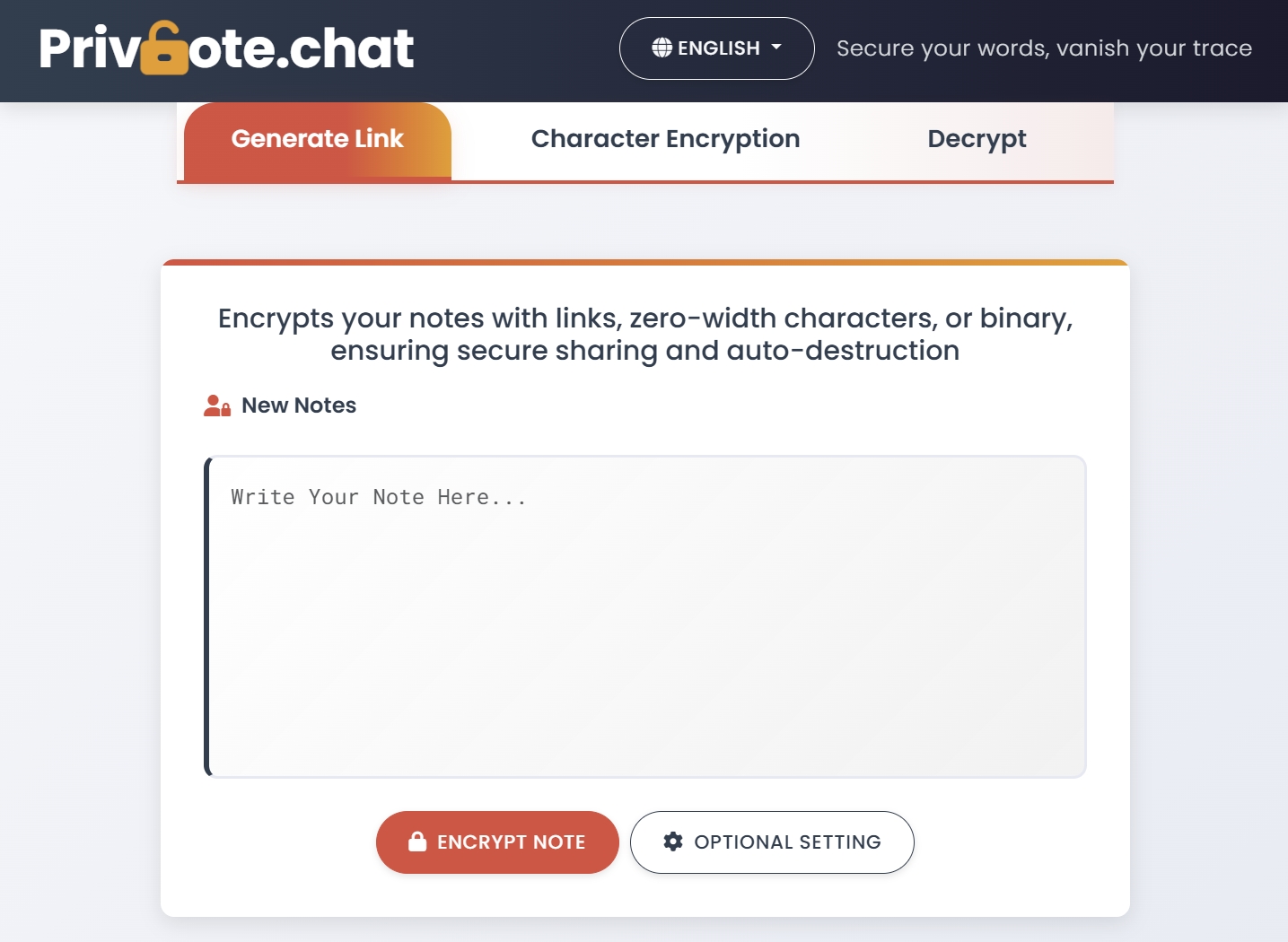
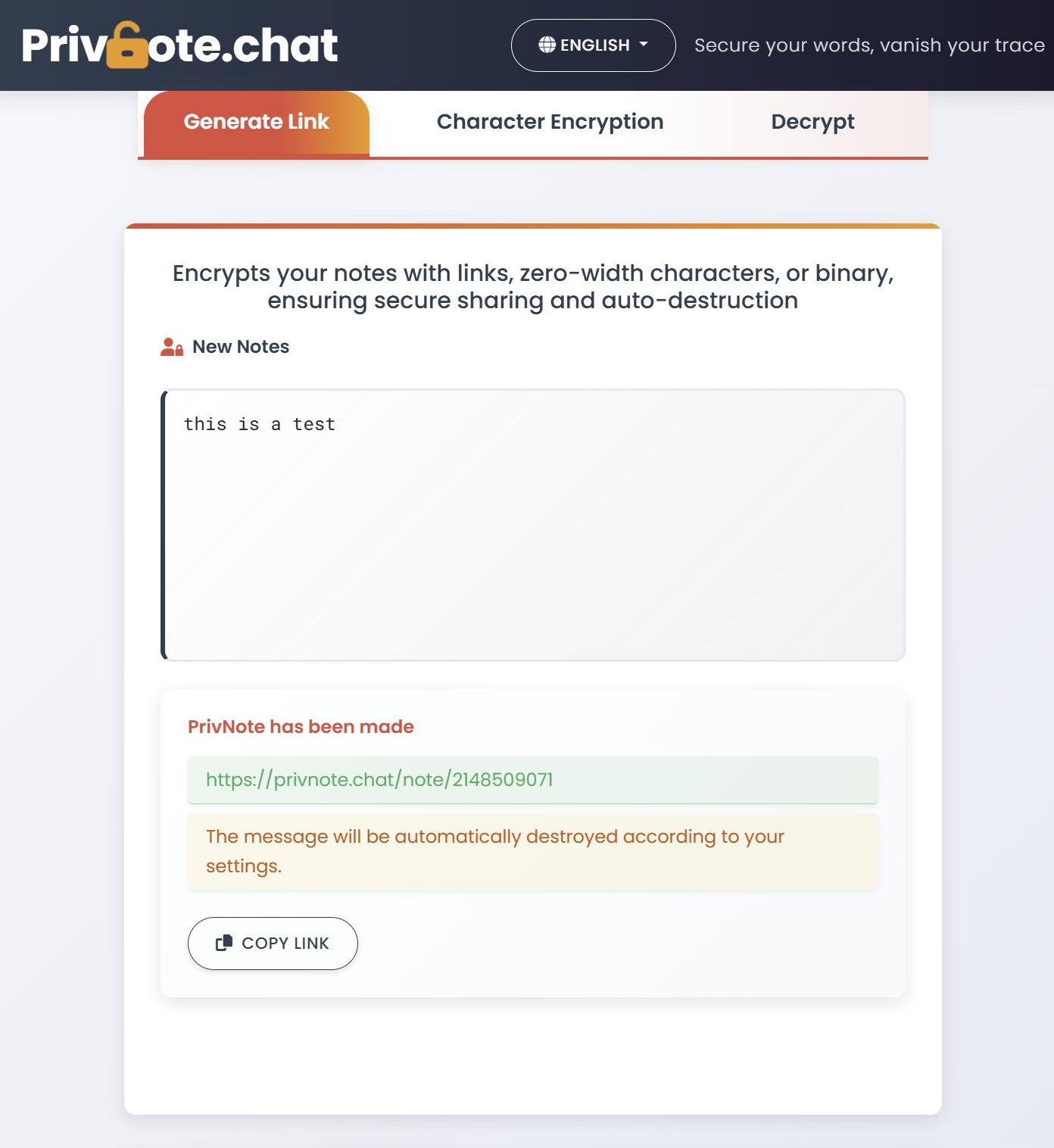
Self-Destructing Notes: The Beginner-Friendly Approach to Secure Messaging
For newcomers to secure messaging, self-destructing note services like Privnote offer an excellent entry point to privacy-focused communication:
Why Self-Destructing Notes Are Ideal for Beginners
- No technical knowledge required: Simply write your message and share a link
- No software installation: Works in any web browser
- No account creation: Start using it immediately without signup
- Intuitive concept: The idea of a message that disappears after reading is easy to understand
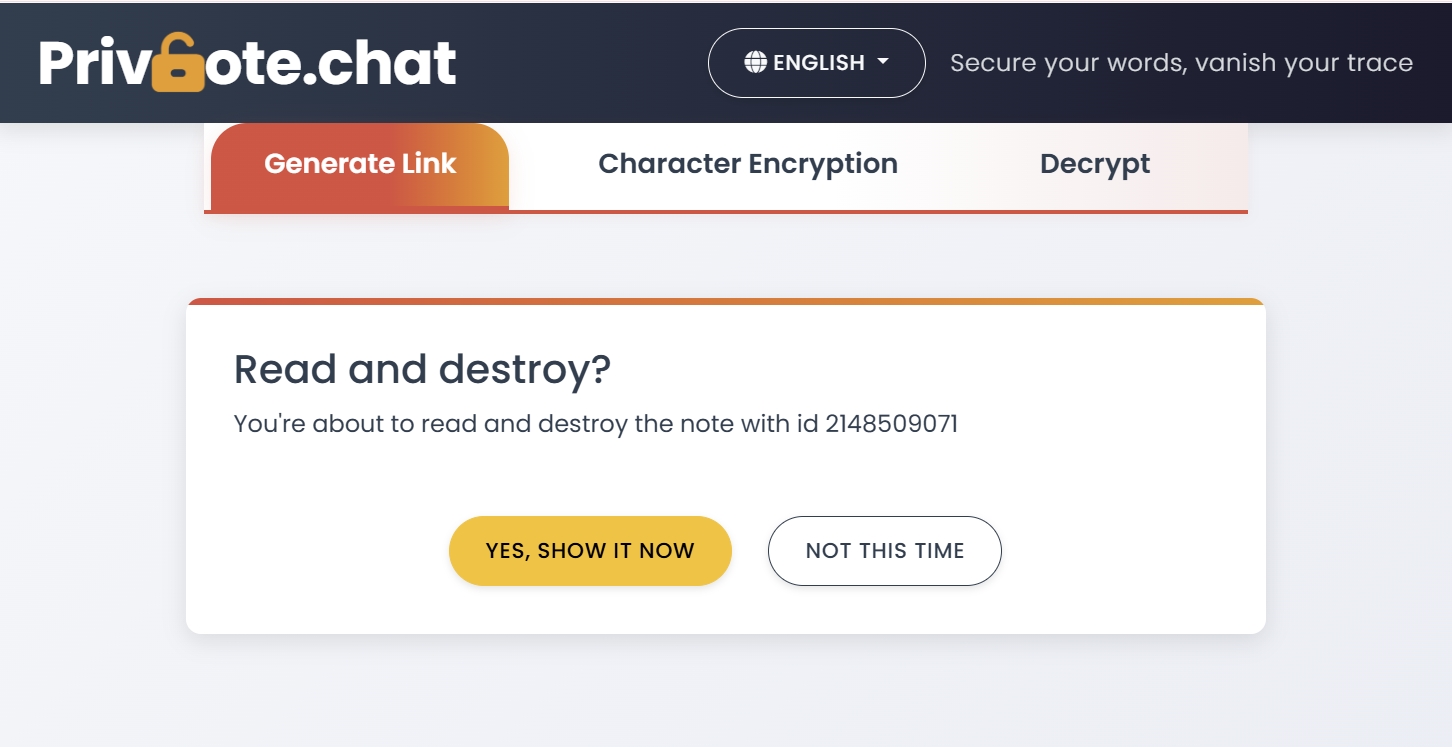
How Self-Destructing Notes Work
- You create a note with your sensitive information
- The service encrypts your note and generates a unique URL
- You share this URL with your recipient through any communication channel
- When they open the URL, they can read your message once
- After being viewed, the note is permanently deleted from the server
- The URL becomes invalid, preventing future access
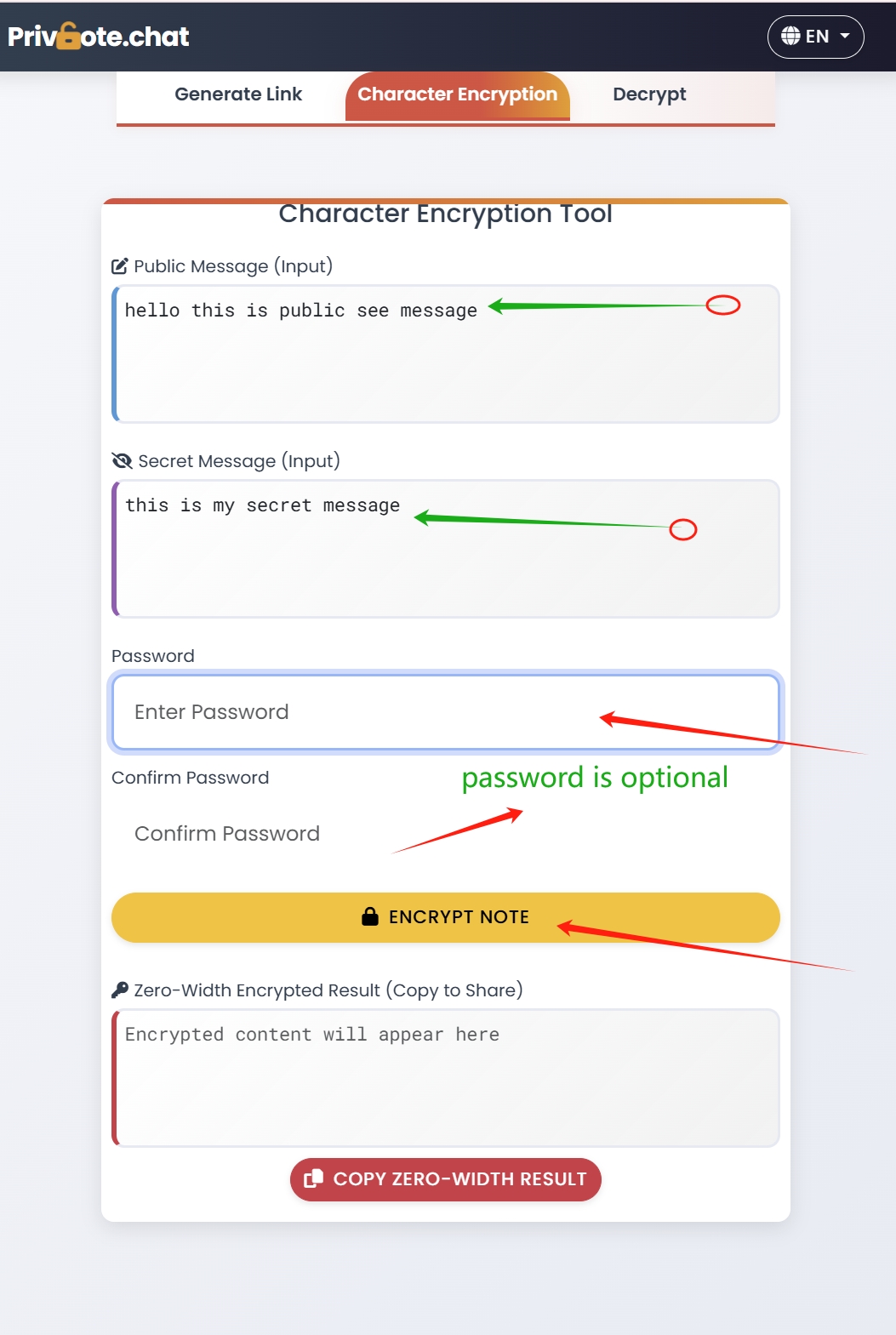
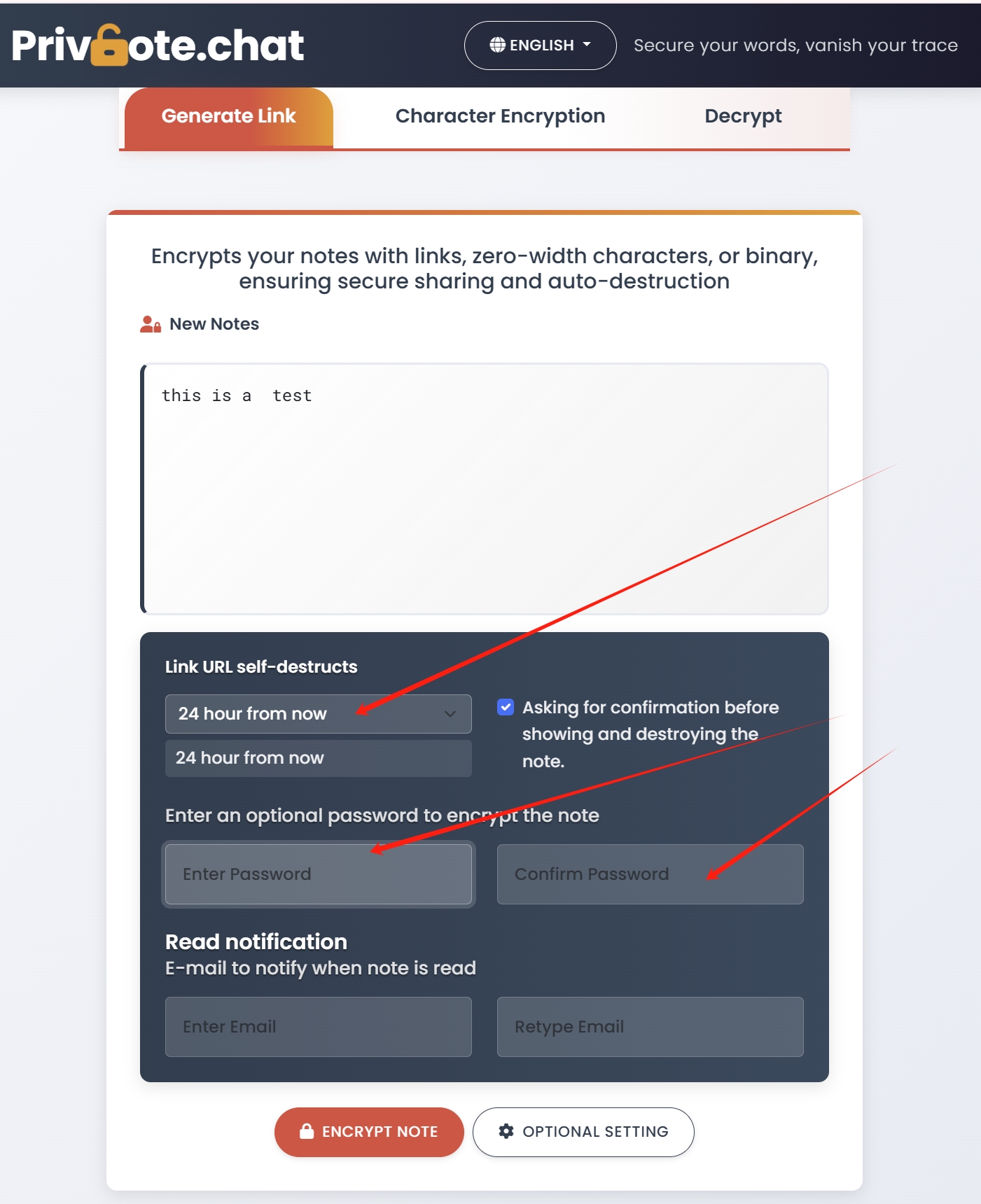
Additional Security Features of Advanced Self-Destructing Notes
Beyond basic functionality, look for these enhanced security options:
- Password protection: Require a password to open the note
- Expiration settings: Set notes to expire after a certain time even if unread
- Read receipts: Receive notification when your note has been accessed
- Enhanced encryption: Options like zero-width character or binary encryption
Practical Guide: When to Use Different Secure Messaging Methods
Different situations call for different security approaches:
Use Self-Destructing Notes When:
- Sharing passwords or access credentials
- Sending financial information (account numbers, etc.)
- Communicating personal identification details
- Sharing sensitive information with someone you don't regularly message
- Sending information that shouldn't be stored permanently
Use Secure Messaging Apps When:
- Having ongoing private conversations
- Communicating regularly with privacy-conscious contacts
- Sharing sensitive photos or documents
- Participating in private group conversations
- In situations where message timing is important
Use Encrypted Email When:
- Formal communications that need some record
- Longer-form messages that aren't extremely time-sensitive
- When you need message threading and organization
- Communicating with organizations rather than individuals
Consider Standard Messaging Only When:
- The information is not sensitive or personal
- The conversation would not be problematic if made public
- Convenience outweighs privacy concerns for that specific exchange
Security Habits for Better Messaging Privacy
Even the most secure messaging tools require good privacy practices:
Device Security
- Keep your devices locked with strong passwords/biometrics
- Install security updates promptly
- Use security software to detect malware
- Be cautious about which apps you install
Account Protection
- Use strong, unique passwords for messaging accounts
- Enable two-factor authentication whenever available
- Regularly review connected devices and active sessions
- Be alert to signs of account compromise
Message Discipline
- Regularly delete sensitive message history
- Verify recipient identity before sending sensitive information
- Be cautious about message forwarding
- Use appropriate security levels for different types of information
Privacy Habit Tip
Before sending any message, take a second to ask: "Would I be comfortable if this message was accidentally made public?" If the answer is no, consider using a more secure communication method.
Getting Started with Secure Messaging Today
Here's a simple action plan to improve your messaging security right away:
Step 1: Audit Your Current Messaging
Take inventory of what types of sensitive information you're currently sharing through standard messaging channels.
Step 2: Try Self-Destructing Notes
The next time you need to share something sensitive (like a password or personal information), use a self-destructing note service like Privnote instead of your regular messaging app.
Step 3: Consider a Secure Messaging App
For ongoing secure conversations, install a privacy-focused messaging app and invite your most frequent contacts to join.
Step 4: Develop Better Habits
Begin practicing the security habits outlined above, focusing first on proper handling of your most sensitive information.
Conclusion: Balancing Security and Convenience
The key to sustainable messaging security is finding the right balance between protection and practicality. Start with securing your most sensitive communications using simple tools like self-destructing notes, then gradually build more secure habits as you become comfortable with the concepts.
Remember that perfect security doesn't exist, but significant improvements are easily within reach. By understanding the basics of messaging security and implementing appropriate tools for different types of communication, you can dramatically reduce your digital vulnerability while still enjoying the convenience of modern messaging.
Ready to take your first step toward more secure messaging? Try creating a self-destructing note with Privnote the next time you need to share sensitive information.